If every website could have its way, it would only be visited by genuine customers. Among many other things, this means they seek to combat anyone from fraudsters — understandable — to bots and web scrapers from interacting with their site. Both impact their bottom line in various ways and, as a result, there is a market for services that are geared towards being able to distinguish an ordinary visitor from a risky or suspicious one.
At the same time, people who want to engage in web scraping for myriad reasons also want to be able to test their IPs and setups to see whether they fit the mold of an “ordinary” user. Say you’ve just bought your first proxy from a provider and want to test it. Those same services offer proxy users a way to test themselves as well, either under the term “IP score”, “IP fraud score”, or “proxy detector”.
In this article, we’ll be exploring two key areas: The first topic we’ll discuss is how IP scoring and proxy/VPN detection work and to what degree these services are correctly communicating to their users what they’re testing. Next, we’ll take a look at the metrics and indicators these services use, which of these indicators are credible, and how credible indicators can sometimes be used to arrive at faulty conclusions.
An IP score, at its core, is marketed as a simple and easy way for someone to determine whether an IP is associated with spam, fraud, botnets, hacking, or generally suspicious activity. Let’s take a deeper look at what these services do, where they fit among services of their kind, what indicators they use to test your IP, and to what extent they’re testing your IP at all.

What is IP Score?
An IP score is a way to express the likelihood that an IP address is associated with fraudulent activity or malicious behavior. This quality score is usually rated on a scale of zero to 100. Websites use IP scoring services to test IPs and emails to identify bots and fraudsters, verify payment transactions, and combat fake registrations — even dating scams. Any incoming traffic that doesn’t pass the sniff test gets blocked.
IP score services exist on a spectrum of digital identification services that start at IP lookup services and progress to increasingly broader — and more complicated — services like browser fingerprinting. As one moves from one end of the spectrum to the other, indicators move from being solely based on IP address to a wider range of non-IP-based indicators. This comes coupled with an increasing amount of contextual interpretation.
Digital Identification Services
The spectrum, for the purposes of this article, looks like this:
- IP Lookup
IP lookup services rely solely on your IP address to provide information on its geolocation, including country, region, and city; autonomous system number (ASN), which includes the name of the ISP; and basic additional information. They just provide identification of an IP without passing judgment.
- IP Score
IP score services generally look at the same information as an IP lookup service and then test this data against blacklists, historical data, and other indicators. Each red flag is then subtracted from your score — or added up depending on the service. They assess the risk level of your IP based on their findings.
- Proxy Detectors & VPN Detectors
Services styling themselves as proxy detectors or VPN detectors go one step further than analyzing your IP. Alongside IP-based data, they also use browser-level indicators, like user agent strings, and perform open port scans. The purpose is to identify signs that you are trying to anonymize your online presence.
- Browser Fingerprinting & Bot Detectors
Browser fingerprinting services encompass the broadest analysis of a user, including network, device, and browser-related indicators. They use all the data a proxy detector does and go significantly further, collecting browsing fingerprints like plugins and fonts, device information like how your hardware renders graphics, and network information like ASN and geolocation details. The purpose is to create a unique profile to help track you across websites for marketing and fraud detection purposes.
Most businesses started small and expanded their products or services as they evolved. A service that started as an IP lookup may start testing that data against blacklists; an IP score service might move to offer proxy detection services, etc.
Problems arise when those shifts are not properly communicated and a service is actually performing one job within the terminology of another. By the end of this article, we hope you’ll be able to see a service, determine what category it fits into, and whether it’s doing a credible job.

IP-Related Metrics
An IP score is a way for websites to determine the risk level of an IP. This is derived from the IP’s geolocation, what ISP the IP is associated with, network characteristics, and whether the IP address is listed on any blacklists.
Simply put, it’s a very low-impact way to gauge whether a given user accessing their services is legitimate or a fraudster up to no good. This can impact whether or not the user is able to register a new account, make a payment, and more. If your IP is deemed to be risky, this might trigger additional levels of verification (two-factor authentication, for example) or be outright blocked.
Indicators used for IP quality scoring include:
- Geolocation: The physical location of the IP address.
- ASN (Autonomous System Number): The ISP, carrier, or organization associated with the IP.
- DNS Records: DNS resolution history, including the DNS servers used.
- Historical Behavior: Reviews the past activities associated with the IP and tests it against blacklists.
All IP score services use these metrics — some go a step further which we’ll discuss later — to arrive at a score of some sort. Each of them is interpreted and assigned a risk score of some variety.
Most IP score services will start by assessing your IP on its own merits. This involves checking each of the aforementioned points without accounting for broader context.
The geolocation of an IP is generally a neutral data point in this instance. It simply expresses where your IP is located. Next, the service will look at the IP’s ASN. This will show the ISP or carrier the IP is registered with. Here, the service is looking for the source of your IP, whether it is residential or a datacenter in origin. A non-residential IP is generally considered to be associated with more risk.
Next, the service will do a reverse DNS search, which translates the incoming IP into a domain name. The domain is tested against DNS blacklists to identify email fraudsters and combat domain spoofing.
Finally, the IP is tested against an assorted number of blacklists, to see whether they have been flagged for behavior in the past. These include Spamhaus, Barracuda, Spamcop, and Project Honeypot among many others.
This would be a credible way of testing an IP on its own merits. There are also further contextual tests that can be done that may also be considered credible. Here, nuance is important, as these are results that do not reflect directly on the IP but are still related to the IP.
This includes checking IPs from the same ISP against blacklists. While this does not express an opinion of the IP itself, it can help paint a more detailed picture of whether an ISP is associated with more risk-tolerant IPs.
A second contextual piece of information is the broader context of the IP’s geolocation. If the IP originates from a neighborhood known to house scam fraud centers, it may be legitimate to include this piece of information when relaying the IP’s score. The danger here is that one can be considered guilty by association, as some IP score services flag any IP originating from Russia, for example, as posing an inherently greater risk.
An important caveat is that contextual information should be relayed to the user as separate pieces of information, not bundled together in an IP score, as they are not derived from the IP itself.
One example of an IP score service that makes this distinction clear is Scamalytics. They readily admit when they have no direct information about the IP itself but are willing to make inferences about the IP’s quality based on the ISP that operates it, whether the IP is residential in origin, etc.
Let’s take a look at the following fraud score for a shared proxy.
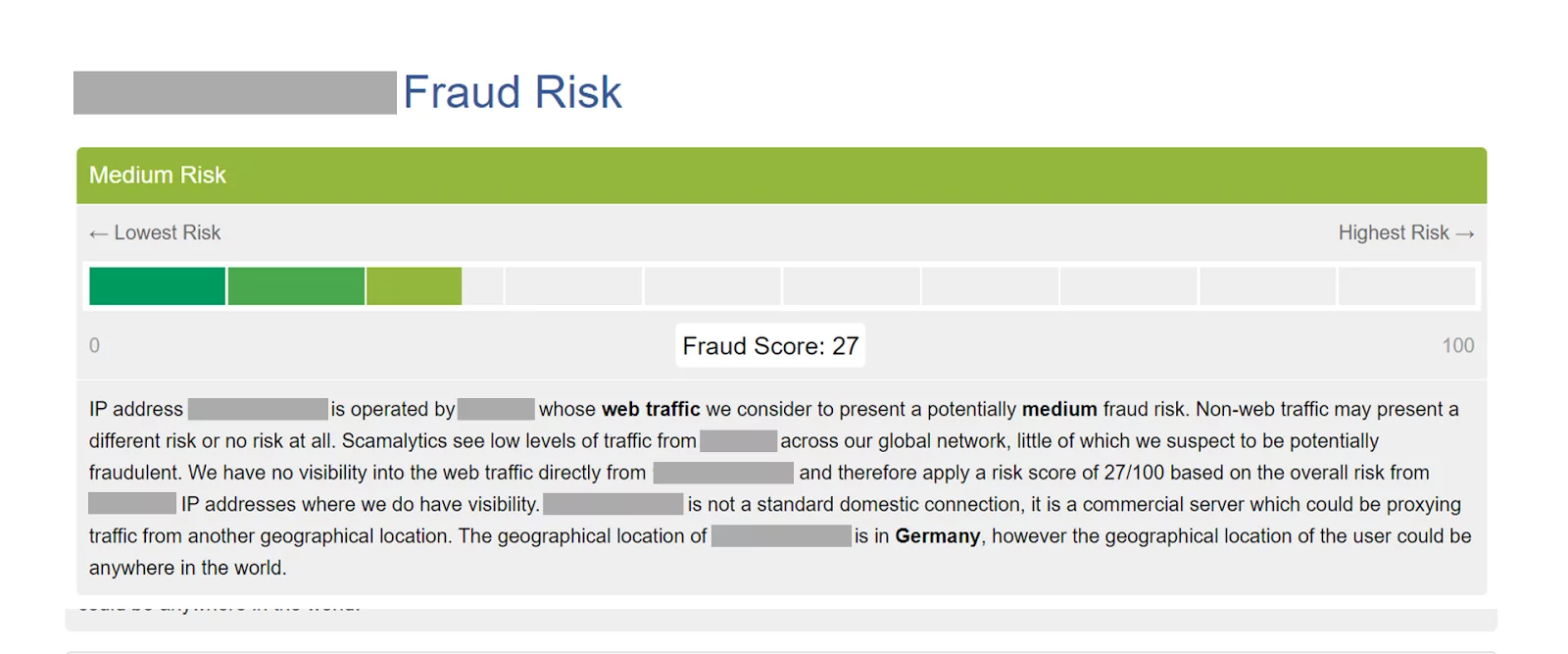
As you can see, Scamalytics do not express their rating as an IP score but as an IP fraud score instead. They clearly state that they have no insight into traffic or behavior from the IP itself and are basing their 27/100 score on their assessment of the ISP. They also add that the IP originates from a commercial server.
This is where we are confronted by the diverging interests between these services and proxy users for the first time. A datacenter IP isn’t necessarily inherently more risky, but a service catering to websites will err on the side of caution. The fact the IP is coming from a commercial server doesn’t inherently mean it’s a proxy server either, but for a service calculating fraud, caution is the priority.
One can take issue with their fraud assessment of the ISP; it’s a valid criticism. The point being illustrated here is the clear communication of what the score is based on.
A completely anonymous profile starts
with the highest quality mobile proxies

Proxy/VPN Detector vs IP Score
Proxy detectors and VPN detectors serve a different purpose to IP score services and this is where the majority of users’ confusion arises. To determine whether someone is using anonymizing technology, VPN and proxy detectors will not only look at geolocation, ASN, DNS settings, and blacklists, but also use browser-level metrics, open port scans, traffic fingerprinting, and WebRTC tests.
The services of an IP scorer and a proxy detector are two distinct and different ones, measuring different things.
Why does this matter?
Some IP scoring services have, through the natural process of providing added value to their services, conflated IP scoring and proxy detection. All of the metrics mentioned in this section have absolutely nothing to do with one’s IP. Testing a user agent string to find a mismatch between the geolocation and the device’s time zone settings is not a metric one can measure from just an IP address. But to a non-technical concerned citizen, that distinction is moot.
The same is true of open port scans. Certainly, it stands to reason that a proxy server would have an open port to listen for a client, but that has nothing to do with one’s IP address. Reflecting this fact as increased risk factors in the form of a lower IP score is incorrect.
Some services do an admirable job of noting the difference between these services; others do not. Being able to identify which site is testing your IP and which is going beyond that is important.
Browser-level indicators include:
- Basic browser fingerprints like user agent string
- Open port scans
- Reverse DNS lookups
- Traffic fingerprinting
Let’s use the popular service ip-score.com to illustrate everything we’ve been talking about.
First, I visit the website and, as expected, my IP scores 100/100.
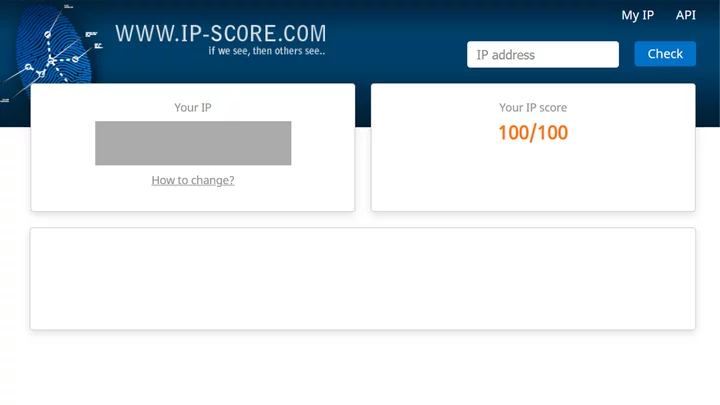
Next, I manually change my time zone on my computer to somewhere several hours ahead. I revisit the site.
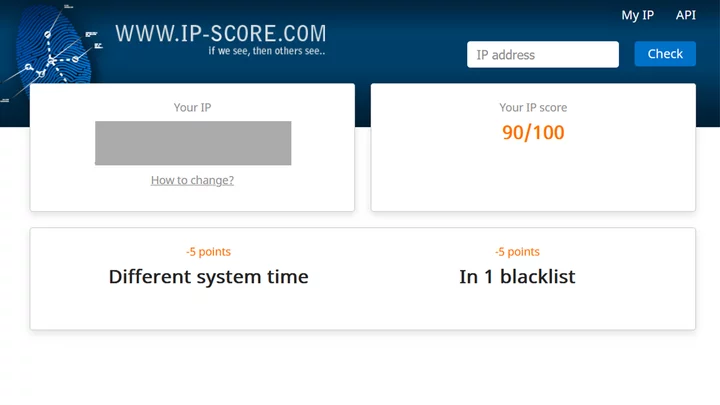
My IP remains unchanged. Suddenly I’m on a blacklist and the site has seen the (browser-level) inconsistency between my device’s geolocation and my time zone settings.
Next, I use an antidetect browser without using a proxy to intentionally create a nonsensical profile that doesn’t suppress WebRTC.
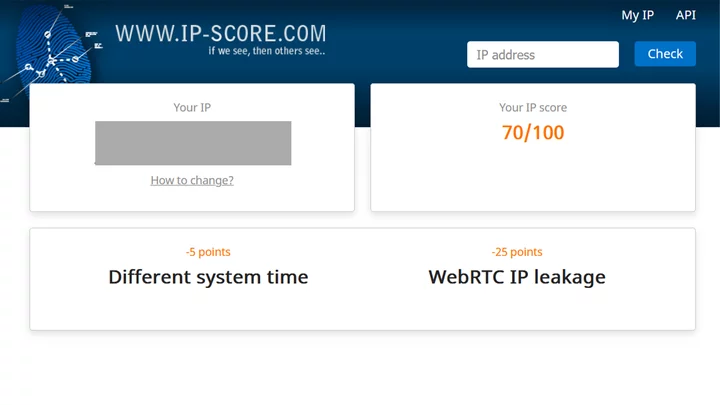
As if by magic my IP — which has remained the same throughout this exercise — has suddenly dropped to 70/100. Furthermore, I’m no longer on the blacklist I was on 5 minutes ago.
Let’s exit out of the antidetect browser and go back to the same site.
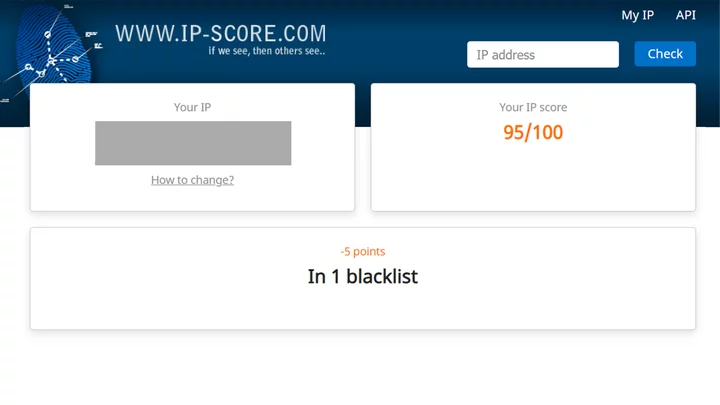
I am now back on the blacklist and my IP has dropped to 95/100 from its original perfect score, all without having changed my IP or done anything other than (incorrectly) use an antidetect browser and visit this website.
In short, the only thing this website can really tell me about my IP is whether I’m on a blacklist.
Watch now as I run a heavily used IP that’s listed on a free proxy list through the ip-score system.
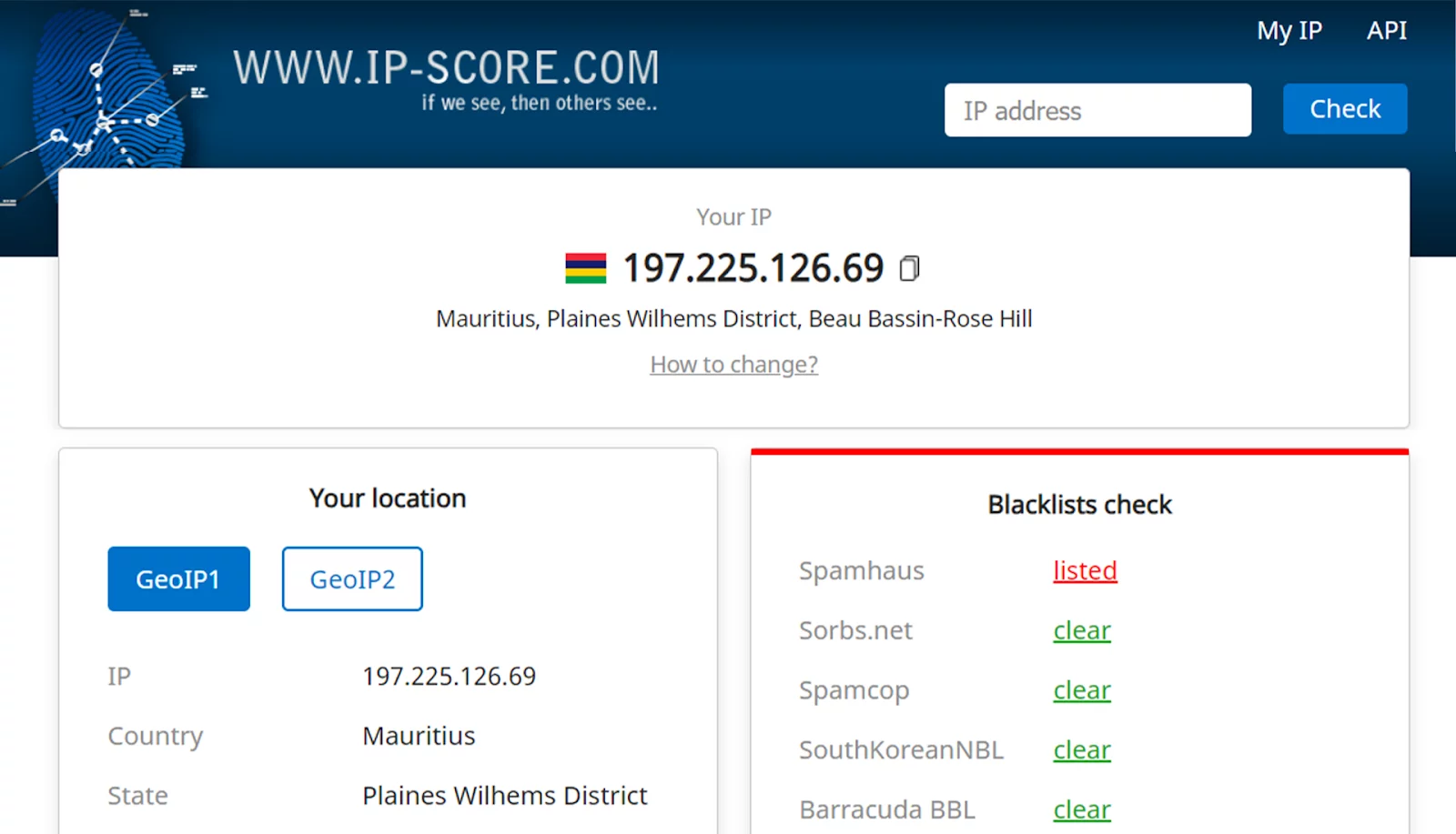
Isn’t it strange how it’s no longer able to give the IP a score if I’m not testing an IP I’m currently using? This is because the service is not testing the IP as such, but testing it against non-IP related indicators it’s picked up from my browser.
For contrast with the earlier proxy, let’s run this same free proxy through Scamalytics.
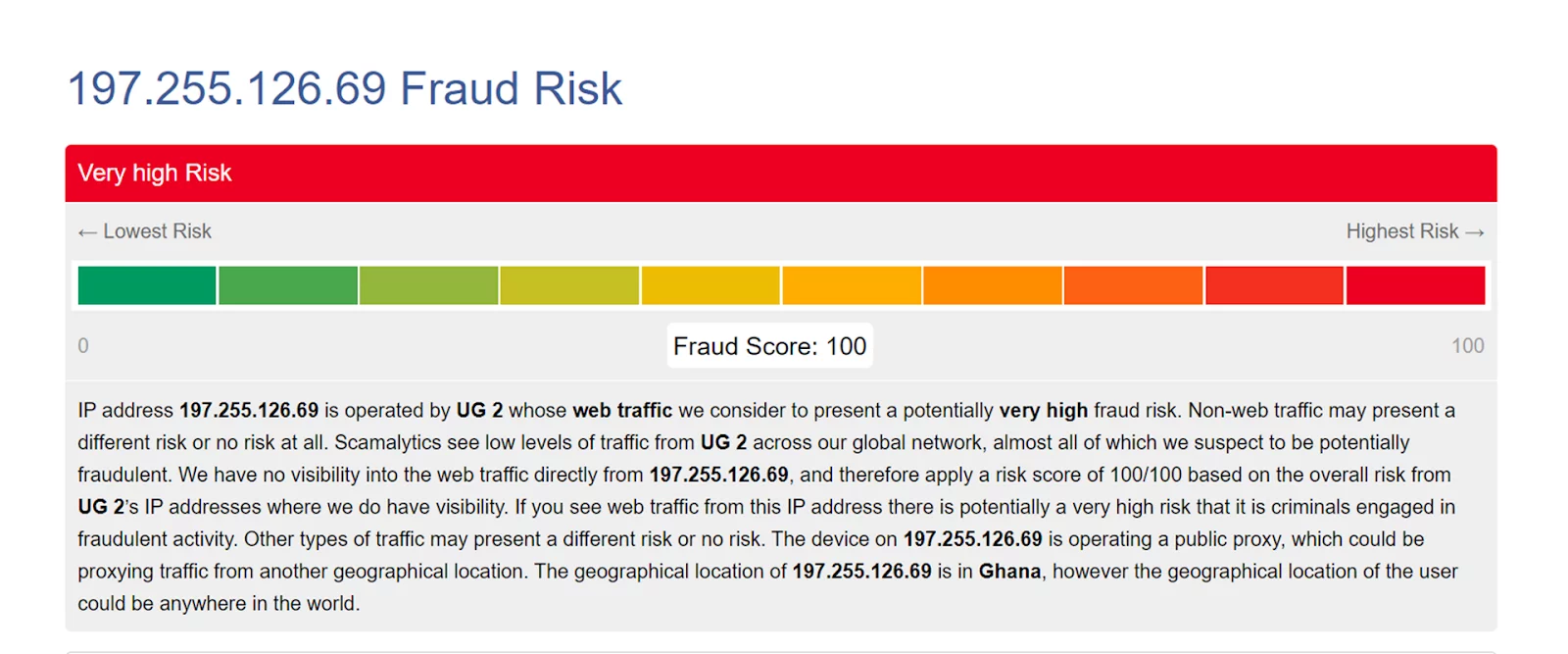
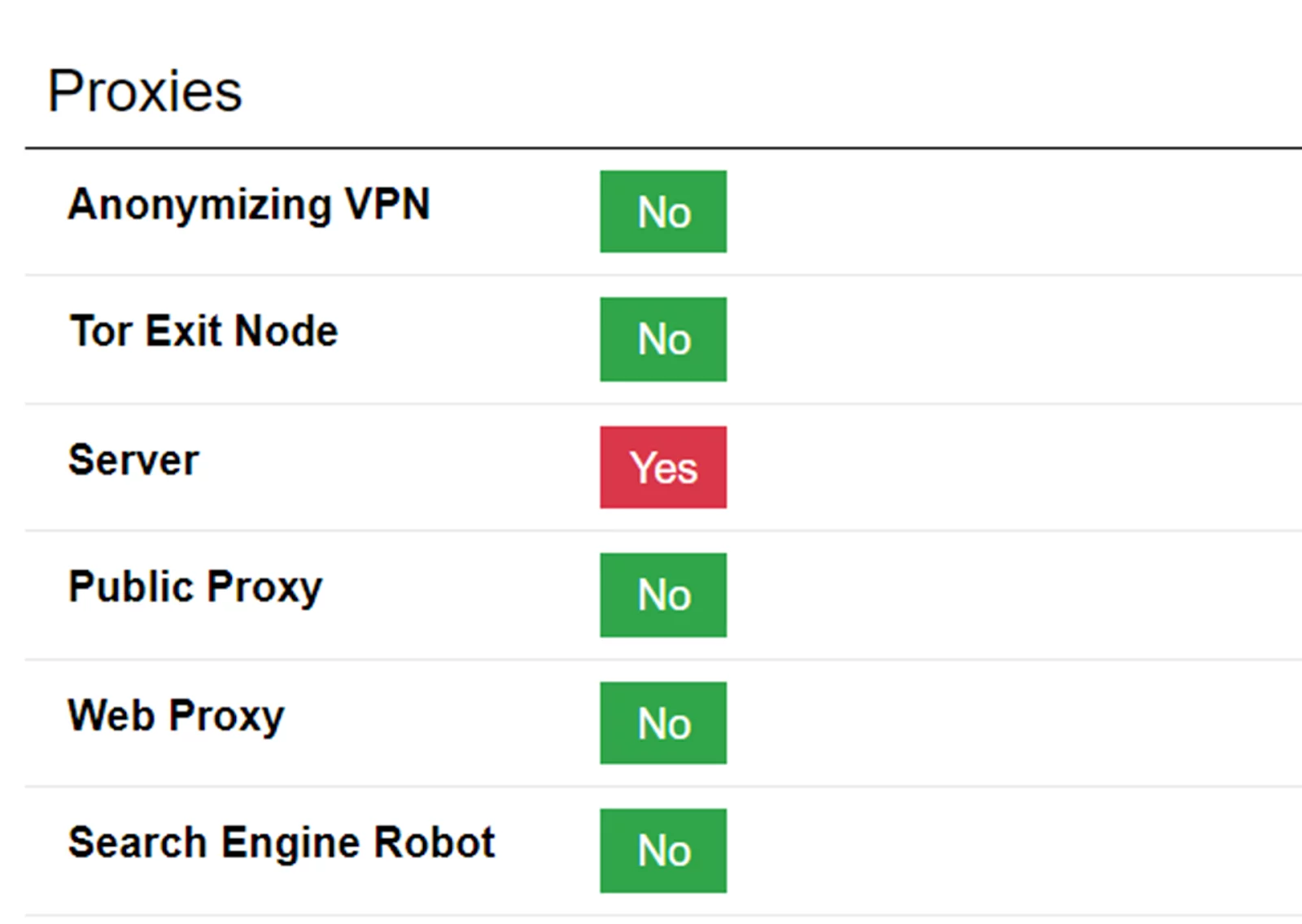
As you can see, every red flag is going off based on the ISP, UG 2. Alongside the text, Scamalytics’ proxy detection shows us this.
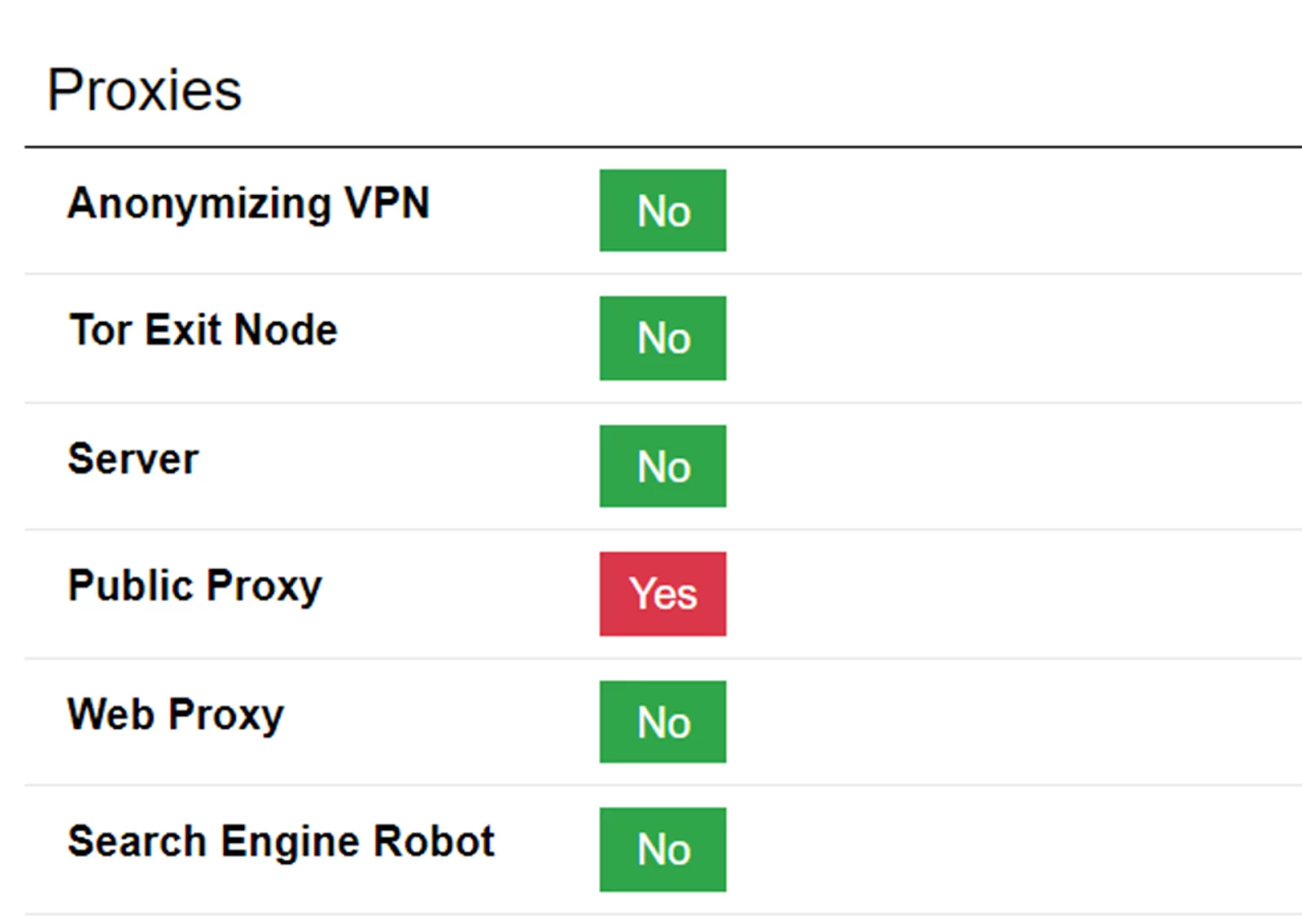
Compare this to our German proxy from earlier, which did not get flagged explicitly as a proxy, but simply as a server.
The Problem with Proxy Detectors
The same lack of clarity and transparency in how an IP score service arrives at its conclusions applies equally to services that do proxy detection and VPN detection. Again we come back to the diverging interests of websites seeking to assess the risk associated with a visitor and a proxy user who wants to self test.
To illustrate this, let’s take a look at SEON, a remarkable service that offers its customers ways to combat fraud and money laundering. As they say themselves, “using email, phone, and IP data collected” they can create a detailed digital footprint of visitors to flag potential flight risks before any damage is done.
On their website they give you the opportunity to test out your own IP’s fraud score, something that factors into one’s overall fraud score. At the risk of beating a dead horse, let’s put our German IP through it and see what it shows.
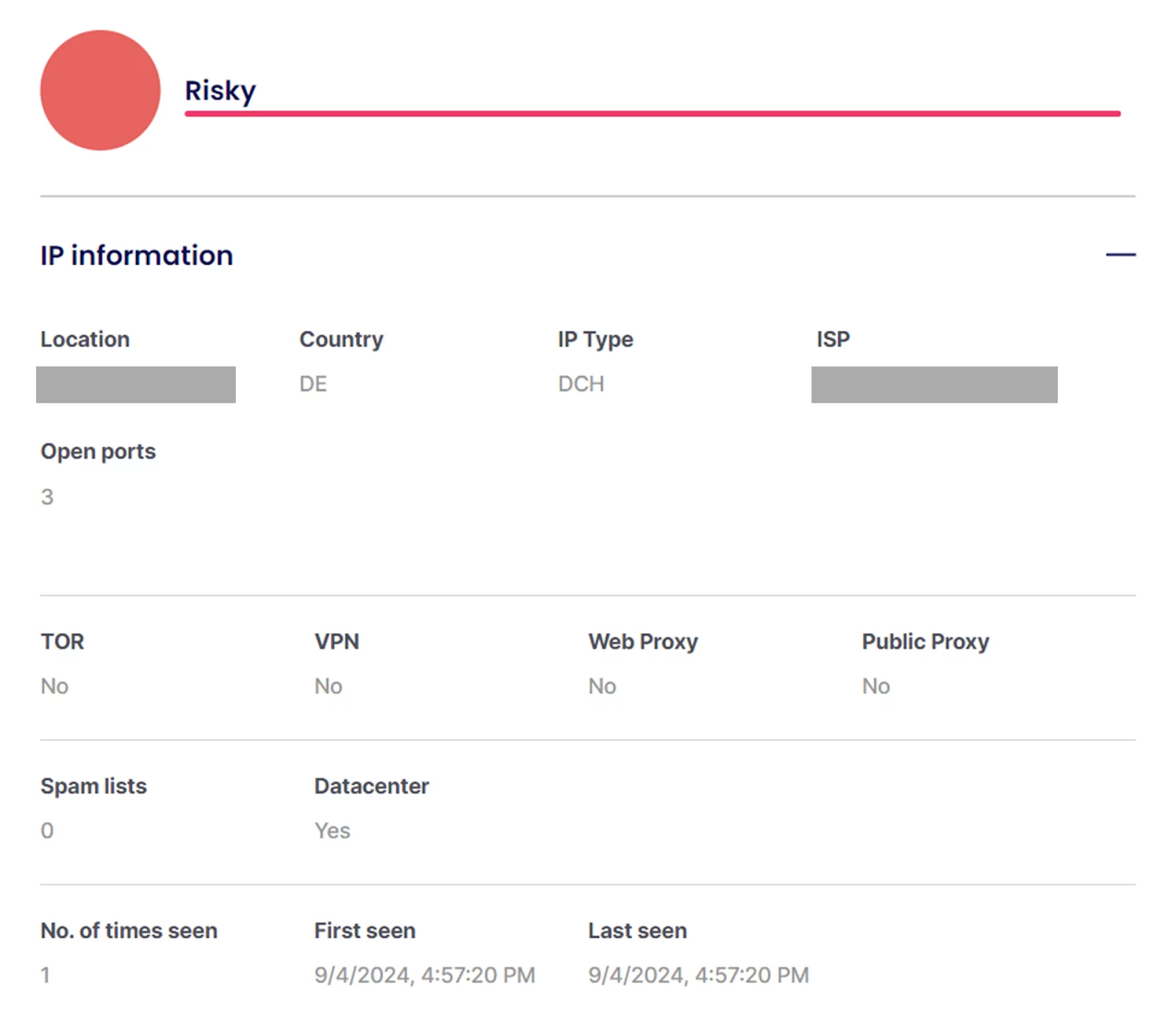
Similarly to our previous tests, the IP is flagged as originating from a datacenter server. Despite the fact the tests for anonymizing technology come back negative — as shown by the row of “No” — it still classifies the IP as “Risky”. While SEON doesn’t break down how they arrive at this conclusion directly, we can figure it out from one of the screenshots from their blog.

From this we can learn more about our “Risky” rating. In fact, it’s quite similar to our previous results from a different service: The fact it’s a datacenter IP counts against it, as does the fact it has three open ports.
The final line in our test is arguably the most concerning of all, and raises many red flags: “No. of times seen”.
This begs the question: What if these services, who clearly prioritize caution over accuracy, use their services to also track curious proxy users who test their IPs? To what degree does the number of times an IP is searched factor into its rating?
While we have no concrete evidence one way or the other, the lack of transparency is in itself concerning.
Let’s move on to exploring the next level of identification services, browser fingerprinting, and how they differ from proxy and VPN detectors.
Proxy/VPN Detection vs Browser Fingerprinting
Browser fingerprinting is the process of collecting data from a user’s browser, IP, device — including hardware and operating system — and other sources to create a unique profile of that user. Most commonly performed by websites in order to offer up personalized ads, it is also an effective method to combat fraud and identify bots.
Browser fingerprinting services, including bot detectors, serve the latter purpose, using browser fingerprinting to identify users using more anonymizing technologies than just a proxy or VPN. Browser fingerprinting services will measure and check the following:
- IP address
- Geolocation
- Browser information
- Software information
- Hardware information
- Bot detection
- DNS leaks
- WebRTC leaks
- Blacklists
- Anonymizing technology
Software information, in this context, can be anything from checking your operating system and type of browsers to the fonts installed on your device. Likewise, hardware is everything from how your browser and hardware render images, your screen resolution, and how much memory your device has to the brand and model of your processor.
Each of these data points and the way they interact with each other is used to create a unique fingerprint and goes far beyond our IP score services from earlier. VPN and proxy detection comprises only a fraction of the tests a browser fingerprinting service performs.
Bot detection in particular goes one step further and analyzes one’s browser environment, searching for signs of automation tools like Selenium, Puppeteer, and Playwright. This includes looking for simulated browsers, signs of deception in the navigator, and automated user actions. Many of these services will distinguish between good bots like Google crawlers and bad bots, including web scrapers.
None of these indicators are related to IP address. Having a “high quality” IP will not help a scraper that does not successfully pass these checks — it will still be flagged as a bot. By contrast, a scraper that perfectly passes each of these checks that uses a heavily used, blacklisted IP will still be flagged as fraudulent traffic, and that will have everything to do with appearing on blacklists.
Conclusion
While IP score services may seem like a convenient way to check the quality of your IP, it’s a lot more complicated than that. Many of these services go beyond IP-based analysis, using browser-level indicators that are then expressed as a criticism of the IP itself. This lack of transparency and poor communication can result in an uncritical user walking away with completely incorrect conclusions.
As a user it’s important to be aware of what the service you’re using is testing, how it’s arriving at those conclusions, and the data it’s using to get there. It’s also important to keep in mind that most of these services cater towards websites, and as a result will always prefer to incorrectly flag legitimate traffic as risky than the reverse.
A very brief summary of what each service should do:
An IP score should test:
- Your IP against blacklists
- ASN-related information like ISP
- Geolocation
The service is detecting a proxy or VPN when it’s looking at:
- Basic browser fingerprints
- WebRTC leaks
- Open port scans
The service is a bot detector and browser fingerprinting when it’s looking at:
- Signs of automation
- Hardware information
- Graphics rendering
In short, each of these services serves a specific purpose, generally catering towards websites trying to combat automation and fraud. As a proxy user or botter trying to self-test your IP, keep in mind what the service is checking. At the end of the day, the further removed you are from a “normal user”, i.e. a residential IP from a home computer or mobile phone, the more red flags will start to go up.




