
Buy mobile proxies based on a network of thousands of real mobile devices and access to millions of mobile IPs.
Unlimited Data
Fair usage applies
Up to 100 Mbps
Depending on plan
50 locations
in the United States
14-Day Money-Back
Guarantee

Massively Scalable
Whether you need thousands of unique proxies, or terabytes of data, the Proxidize mobile proxy network can handle it all.
Dedicated Hardware
Based on Proxidize hardware that we develop, manufacture and manage in-house, ensuring we have 100% control over the entire supply chain.
City Targeting
Access up to 50 cities and switch locations instantly with our intelligent city-level targeting system, or let the system decide intelligently for you.
Carrier Targeting
Target any of the available carriers directly from your dashboard to ensure IP diversity or let the system select the carrier for you via our intelligent routing mechanism.
HTTP and SOCKS
With support for both HTTP(s) and SOCKSv5 proxies, you can rest assured that the proxies will be easy to use.
Unlimited Data
Truly unlimited data that never stops. Enjoy full-speed browsing for all your key needs, and once you exceed the fair usage, you’ll stay connected, but you may be deprioritized.
Rapid IP Rotation
With near instant IP rotation, averaging 1-3 seconds, powered by a proprietary rotation mechanism, you will never have to worry about rotation downtime.
Instant Delivery
Zero setup time means your mobile proxies will be available instantly after purchase.
We have partnered with dozens of data centers and dedicated hosts to ensure we are in almost every corner of the United States, with more countries available on request.
Any qualified entity can apply to become a Proxidize host via the Proxidize Hosting Program. Contact us to learn more.

With speeds averaging from 5-25 Mbps, and in some cases, up to 100 Mbps, you can be assured that you will never face an issue with the proxy speed. And if you have a specific speed requirement, we can always provide a custom speed SLA on request.

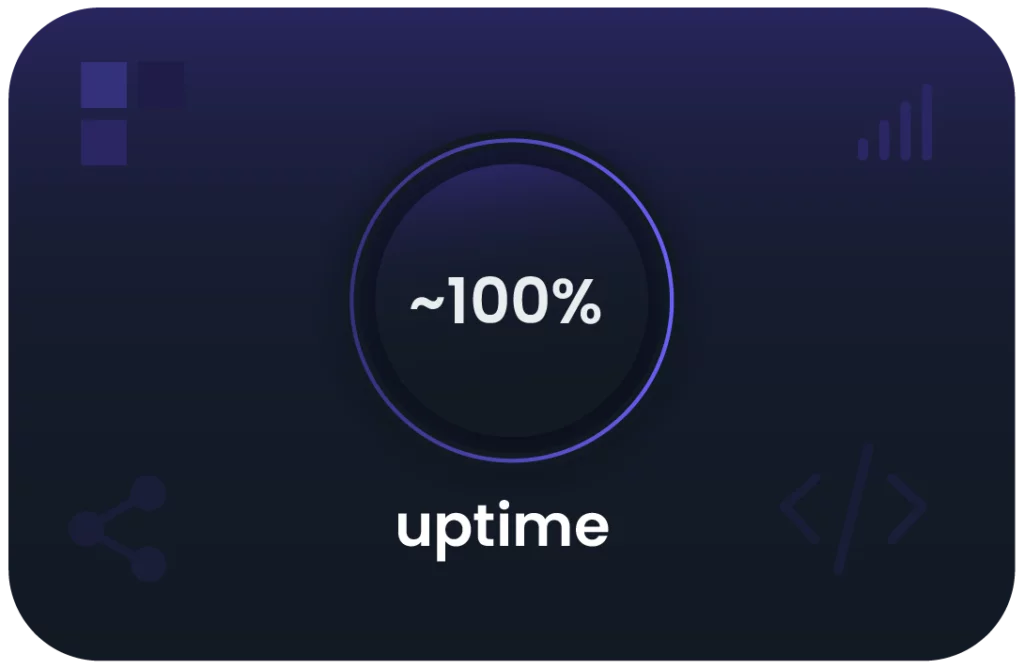
We have spent years perfecting our load balancing and fallback systems to guarantee a near 100% uptime experience. Even if an entire datacenter goes down, you will be switched to a different one automatically and with less than 30 seconds of downtime.
Buy mobile proxies from thousands of real devices with access to millions of mobile IPs.
Pay per Proxy
Best for account management
$59/Proxy/Month
Pay per GB
Best for web scraping
$2/GB/Month
$1/GB/Month
Best for account management
Best for web scraping
GB #
Monthly
More Cities
Our network is always growing and we’re constantly adding more cities.
Custom Speed
The ability to select a specific desired speed band for your proxies.
Available now on request.
Reseller Portal
Very soon you will be able to resell Proxidize proxies to anyone.
Available now on request.
More Countries
Need proxies in Canada, UK, Germany, or else? Those too are coming soon!
Available now on request.
Want more?
If you have any recommended features you would like to see, you can always request them via our public roadmap.
When buying per GB, you can rotate the IP every request or keep the same IP temporarily using sticky sessions.
When buying per proxy, you can rotate your proxy IP infinitely every minute.
Buying a single proxy does not require KYC. We may require KYC from certain buyers depending on their order size.
We allow all legal use cases, except those relating to the adult industry in any capacity.
Proxidize Proxies run on multiple nationwide premium mobile network operators. We never use MVNOs or resellers. You can select which mobile carrier your proxy uses from your dashboard.
Yes, we support city-level targeting with both per proxy and per GB mobile proxies.
Yes, we offer bulk discounts. Please contact us for more information.
We have built an automated fallback system that constantly monitors the proxies, and if your current endpoint fails for any reason, you will be automatically switched to the next available one in a few seconds, without noticing any changes to your proxy details.
Yes, but this is currently only available for enterprise plans.
Yes, you can buy up to thousands of proxies in increments of 1. Please contact us if you don’t see your desired plan.
You can access all our locations by changing the proxy city from the dashboard. When using per proxy, you can only access 1 location at a time. But when using per GB you can access all locations at the same time.
No, by their nature, mobile IP addresses are dynamic. Meaning there’s no guarantee that the IP will remain unchanged even if you don’t use the rotation functionality.
We only restrict access to any .gov website, other than that, you can access any website using your proxies as long as you have an acceptable use case.
Yes, Proxidize mobile proxies are truly unlimited and you will never be cut off for high data usage. However, we may enforce a fair usage policy of 50 GBs of data usage per proxy per month. This will depend on the total network load for the month as well as the number of proxies. Once the fair usage has been exceeded, we may implement a deprioritization on the proxies, but you will never be cut off, no matter how much data you use.
Mobile proxies, also known as 4G proxies, are a popular choice among people who are active in web scraping and online automation spaces. As opposed to residential proxies, which source their IPs from those assigned to private homes by ISPs, and datacenter proxies, which source their IPs from cloud hosting platforms, mobile proxies source their IPs from those assigned by mobile carriers. This makes it appear as though the user is using a mobile device like a mobile phone, tablet, or dongle.
To be able to effectively explain how mobile proxies work, it’s important to take a moment to explain how mobile network infrastructure works. In this way, we can better understand how mobile proxies effectively leverage the inherent characteristics of mobile infrastructure.
Mobile Network Infrastructure
Mobile network IPs are much more dynamic than other types of IP, due largely to the fact that mobile devices move between cell towers so often. The network is arguably defined by its need to seamlessly assign and reassign IP addresses to devices in a resource-efficient way.
Residential IPs, by comparison, can be both static and dynamic. Even when they are dynamic they usually rotate IPs much less frequently — over the course of weeks, for example. Data center IPs are generally static.
As a consequence of this dynamic IP allocation — and the relatively high number of mobile devices on the network at any given time — mobile carriers need to make the most use of the finite, albeit large, pool of IP addresses they have assigned to them. Enter CGNAT, or carrier-grade network address translation.
With CGNAT, carriers are able to bundle multiple mobile devices onto a single public-facing IP address. Each device has a private IP for internal use within the network and is assigned a public IP that is shared among several devices when interacting with the internet. The experience for the user remains the same. By organizing the network this way, the carrier is able to maximize their use of IP addresses they have available to them (and combat IPv4 address exhaustion). If you want to know more about this topic, check out our article on public and private IP addresses.
Leveraging These Characteristics
Using a proxy server that routes its traffic through a mobile device gives it the characteristics unique to mobile IPs. By using a mobile network, a proxy is able to co-opt these factors, which makes them appear more authentic than their residential and data center counterparts.
This makes mobile proxies unique in several ways:
Mobile proxies in general commonly use either HTTP or SOCKS protocols.
HTTP is the most common protocol, designed to handle any kind of web traffic, like web pages and resources. It works via TCP/IP in a request-response model, where a request is forwarded to a server, and the server sends a response back. The receiver and recipient are only connected for the duration of the request or response, disconnecting in between (stateless connection). By using an HTTP mobile proxy, you introduce that proxy server as an intermediary between your device and the end destination. Your request is forwarded to the proxy who sends it to the server on your behalf, receives the response on your behalf, and then sends it back.
An HTTPS mobile proxy does all the things an HTTP proxy does with the added benefit that it can encrypt the data between your device and the proxy. This has broad implications that we’ve covered in an article about HTTP proxies.
By comparison, SOCKS is specifically a proxy protocol that can handle any type of network traffic, including HTTP but also FTP, and SMTP as well. SOCKS proxies only relay the data between your device and the destination without modifying the content. They also maintain the connection between your device and the server for the length of the session. Importantly, SOCKS5 mobile proxies handle both TCP and UDP, the latter of which is faster. Finally, SOCKS proxies support ways of securing your proxy via authentication, which lets you control access to them.
Mobile proxies come in a variety of types which can be divided into the types of mobile network that they use and which protocols they use. The familiar terms 3G, 4G/LTE, and 5G are different generations of mobile network technology. Each subsequent generation offered improvements in speed, latency, and capacity.
A mobile proxy will naturally be limited to and defined by the specific generation of network technology it’s using. This will have a knock-on effect on what the proxy can be used for. The same is true of the protocol a mobile proxy uses, i.e. an HTTP mobile proxy will not be able to encrypt the data to and from the client.
A residential proxy sources its IP from an ISP, which provides IP addresses to homes. A mobile proxy sources its IP from a mobile carrier.
Both residential and mobile proxies are perceived to have a high degree of authenticity, but where mobile IPs are more dynamic, residential IPs are static or, if they’re dynamic, less prone to changing than mobile IPs. Where mobile proxies use 3G, 4G/LTE, or 5G, residential proxies use DSL or fiber.
Residential proxies have a much larger IP pool available to them, as there are millions of households that ISPs have to provision with IPs, compared to the highly dynamic nature of mobile IPs together with CGNAT.
Yes, mobile proxies are legal in most countries. However, just as with any digital tool, committing a crime while using them is illegal.
If a proxy server is used for illegal activities such as hacking, fraud, or any form of malicious activity, then it becomes illegal. In many jurisdictions, attempting to hide your identity when committing such crimes is an aggravating circumstance. Some activities, such as violating or circumventing copyright laws, can also have legal implications.
Get Your Mobile Proxies Today! Start Now!
Pricing
Company
Products
Resources
Docs
United States
1515 Market Street, Suite 1200 – #822, Philadelphia PA 19102
United Kingdom
85 Great Portland St, London W1W 7LT
All Proxidize hardware is assembled and shipped from the United States and the Netherlands.
© 2025 Proxidize | All Rights Reserved
Discount Applied Successfully!
Your savings have been added to the cart.
Looking to get started with Proxidize? Our team is here to help.
“Proxidize has been instrumental in helping our business grow faster than ever over the last 12 months. In short, Proxidize has empowered us to have control over every part of our business, which should be the goal of any successful company.”

By submitting this form, you consent to receive marketing communications from Proxidize regarding our products, services, and events. Your information will be processed in accordance with our Privacy Policy. You may unsubscribe at any time.