Websites collect an inordinate amount of information from its users. They can do this in ways many of us are familiar with, e.g. cookies and logging IP addresses. Other types of data websites collect can be less obvious, including your device’s operating system, how your graphics card renders an image, and the fonts installed on your computer. All of these elements taken together form a complete image of individual users. This data is used to serve up personalized content feeds, targeted advertising, internal analytics, and for social media integrations, among other things. This creates a situation where you may reject a website’s cookies but still be unknowingly tracked via other methods.
An antidetect browser, also called a stealth browser or privacy browser, is a specialized standalone browser with built-in capabilities to obscure or block websites from collecting this identifying data, which enhances a user’s privacy and anonymity online. On the one hand an antidetect browser spoofs or blocks more static identifiers of a user’s device, like operating system and hardware details. On the other hand, it also compartmentalizes more dynamic identifiers like cookies and session data into different profiles.
Beyond the immediate concerns of privacy, wanting unaltered content feeds, and more, there are a variety of more specific reasons one might want to use an antidetect browser. These can include social media managers who oversee several accounts that can’t be “contaminated” by each other’s data, advertisers who want an unfiltered view of websites where their ads should appear, and e-commerce professionals who don’t want their price analysis to be affected by automated discounts or price hikes when collecting competitors’ data.
This article will delve into how antidetect browsers work and explore some of the leading antidetect browsers on the market today.
Every antidetect browser comprises some core technologies that work together to obscure a user’s identifiable information or present a convincing and consistent alternative profile. There are three broad categories these technologies fall into.
Browser fingerprinting is a way websites collect data to identify users and track them across the internet. Unlike other tracking methods like cookies, browser fingerprinting tracks data about a user’s device that doesn’t require anything to be stored on their device. This makes it harder to detect and arguably more invasive.
There are many data points that contribute to a user’s profile, including:
Antidetect browsers hide or block these data points from being collected by websites in a variety of ways. Many of these features go one step further and allow users to specify what data is sent to the websites, allowing for the creation of customized profiles.
A user agent is a string that a user’s browser sends to every website it visits as part of the HTTP header. The string contains details about the user’s browser type, version, operating system, and sometimes software and hardware details. It is meant to help the server understand the context in which it is operating, enabling it to tailor the response to suit the browser and device capabilities. This is, for example, how a website decides whether to display the desktop or mobile version of the website.
This is an example of a user agent string, which tells a website that it is a Windows 7-based PC using a Chrome browser:
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/47.0.2526.111 Safari/537.36
Antidetect browsers use user agent spoofing to change the information in the user agent string. Often this will be in the form of a pre-set profile but the user agent can be changed manually. Some browsers will offer users the ability to automatically change the user agent at set intervals, too.
Canvas fingerprinting is another way websites can track and identify users. It uses the HTML5 canvas element to draw graphics or text invisibly in the browser. The way the graphics are rendered is unique to each device’s combination of hardware and software, which creates another way for a website to generate a unique digital fingerprint for each user.
Antidetect browsers combat canvas fingerprinting by disrupting a website’s ability to gather consistent data information from the canvas element. There are a few ways they do that. One way is to introduce slight variations to the way the graphics are rendered. A second way is to outright block canvas fingerprinting scripts from running at all. This can sometimes break websites that use canvas for other purposes. Thirdly, the browser can return a blank image, which allows the canvas element to work normally but circumvents the tracking aspect of the image.
WebGL, or Web Graphics Library, is a JavaScript API that allows web browsers to render interactive 2D and 3D graphics without the need for plugins. As it comes standard with browsers, and because the way graphics are rendered very differently based on hardware and drivers, it can be used to generate a unique fingerprint of a user’s device, similar to canvas fingerprinting.
The way an antidetect browser combats WebGL fingerprinting is also functionally similar. This includes spoofing responses from WebGL queries to return generic or randomized GPU and driver models. Alternatively, the browser can limit or block the functionality of WebGL entirely, by extension limiting the information that can be gathered from the data. Doing so might break the website for the user, however.
Websites can detect your local time zone through JavaScript. This information can be used as part of a user’s digital fingerprint to track your location and activities. Anti-detect browsers can change this data to prevent accurate time zone detection and thus help obscure your geographical location.
One way to do this is by overriding the time zone detection to return a consistent, fake time zone. Alternatively, the time zone can be spoofed to match the location of the proxy or VPN being used, which helps avoid the use of a proxy or VPN being detected.
Each of these data points taken on their own would not do much to identify you out of the many billions of people who use the internet, but each of them is a key element in narrowing down the list of variables to be able to identify a specific user and tracking them between websites.
This list covers the most common aspects of spoofing by antidetect browsers. Some go much further, spoofing everything from audio context, fonts, hardware concurrency, and battery API, to name a few.

An IP address is the unique identifying number assigned to every device connected to the internet. IPs are a powerful data point a website will use for fingerprinting.
IPs can be used to identify a user’s approximate location, including country, city, and sometimes even the specific area or neighborhood. Websites use this geographical data to customize content, language, and advertising. They can also be used to infer behavior patterns based on what IP a user is connecting to the website from. This includes the time of day the user is online and the locations they log in from. Furthermore, websites monitor IPs for suspicious activity, such as the same IP logging into several accounts within a short span of time, which might indicate compromised accounts or fraud. Finally, websites can keep track of more stable IP addresses, like a user’s home or office, to link accounts and browser sessions to the same user, even if they are using different devices.
IP masking is the process of hiding a user’s real IP address and showing an alternative one. Two of the most common ways to do so are to use a proxy or VPN. Antidetect browsers often integrate proxy services, allowing users to easily switch between IP addresses. This makes the user appear to be accessing the internet from different locations than they are, disrupting a website’s ability to use IP as an identifying data point.
Proxies are integrated into anti-detect browsers in several ways to enhance user privacy and manage geographic restrictions. Proxies can be configured manually, by giving the browser the IP address and port number. Many antidetect browsers allow proxies to be automatically configured, too. Dynamic proxy switching is also possible, which tells the browser when to switch between proxies based on criteria like time spent on a site, after a set number of pages, and the amount of bandwidth used.
Additionally, proxies can be tied to specific profiles on the antidetect browser, allowing a user to tie proxies to distinct profiles, each with their own compartmentalized cookies and storage. This allows the user to maintain distinct online identities, enhancing privacy and anonymity. One can take it a step further by using a proxy that is consistent with the details such as the time zone of one’s profile.
Despite one’s best efforts to remain anonymous by using a proxy or VPN, sometimes a user’s real IP can be leaked through some technologies or settings — usually ones that bypass one’s browser settings. Antidetect browsers take steps to mitigate that risk in a few different ways, as the following list will illustrate with the four most common causes of IP leaks:
WebRTC Leaks
WebRTC or web real-time communication is the technology that powers many of the browser versions of most of the peer-to-peer audio and video communication applications people use every day. This includes everything from Google Meet and Discord to Facebook Messenger, WhatsApp, and Zoom. It’s so universal because it means no third-party software or plugins are needed.
Without delving too deeply into the mechanics of how WebRTC works, to facilitate the peer-to-peer communication, WebRTC needs to make direct contact with the devices involved. It does this to increase communication efficiency. In the process of doing so, however, it identifies not just the public IP of each device but also its private IP within the local network. Worse still, this can happen even if one is using a VPN if it has not been configured to handle WebRTC traffic properly.
Antidetect browsers account for this by disabling WebRTC outright, but this does mean users lose the functionality of these communication applications.
DNS Leaks
Domain name system or DNS is the protocol that translates websites’ URLs into the IP addresses that computers use to communicate with each other over the internet. DNS queries are not usually encrypted, which means a user’s browser data can be exposed. A DNS leak happens when the DNS queries accidentally bypass your proxy or VPN and are sent through the DNS servers provided by your ISP. This can happen for a number of reasons including a VPN not configured to handle DNS requests properly or if your proxy or VPN doesn’t support IPv6 but your ISP does.
There are a number of ways to mitigate this risk, like manually setting up DNS settings and disabling IPv6. Some anti-detect browsers offer built-in methods of securely managing DNS requests.

Alongside more static identifiers like operating system and hardware details, and network-related identifiers like IP address, there is a third category of more dynamic identifiers that every antidetect browser needs to account for to maintain a user’s privacy. These data points originate directly from one’s browsing activities and include:
Profile management in antidetect browsers is its third pillar. Antidetect browsers allow users to create and switch between multiple browser profiles easily. Each profile operates as an independent browser instance with its own set of data and configurations, compartmentalizing the browser data between a user’s different profiles. By doing so, the users can avoid their browsing activities from being cross-contaminated and being fingerprinted.
Antidetect browser profiles allow users to customize almost every aspect of their identity. Each of the aforementioned spoofing features and proxy integrations can be employed to create distinct profiles for distinct activities.
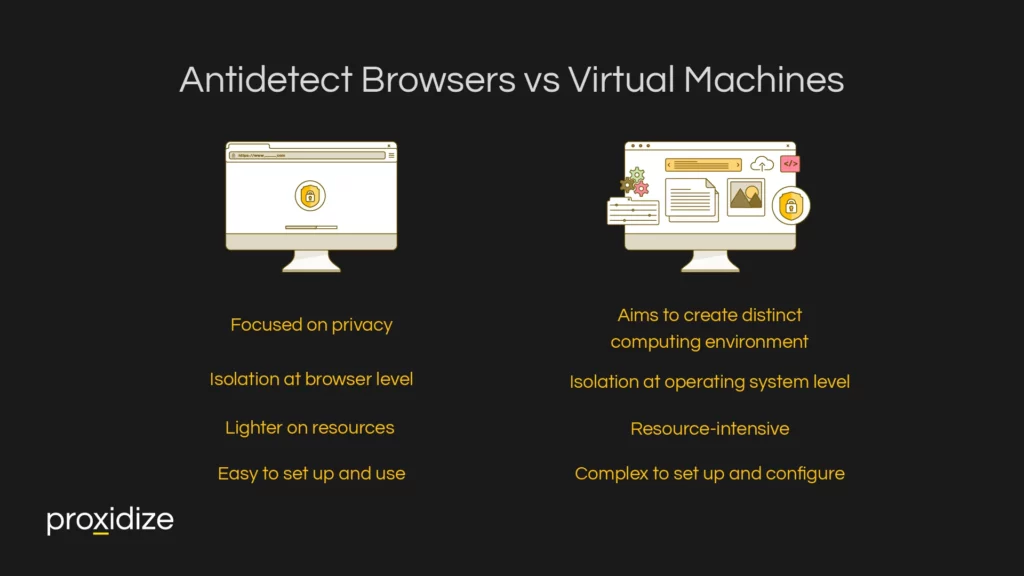
Antidetect browsers and virtual machines might seem similar in concept but they both offer wildly different capabilities. Simply, virtual machines spoof the entire device and anti-detect browsers just spoof the browser. However, there are many more intricate differences between the two.
Virtual machines are software emulators of a physical machine. They create a virtual environment that operates much like a typical computer but allows users to test software and have an easy disposal browser environment for risky content. Each virtual machine operates independently with its own set of hardware resources including CPU, memory, and storage, as well as its own operating system. They provide a high level of isolation, as each virtual machine is completely separated from others, which enhances security and reduces the risks of malware spreading across environments.
The key differences between antidetect browsers and virtual machines lie in their primary use cases, functionality, and the level of isolation they provide:
Virtual machines are practical for someone who needs to test out some programs or only wants to spoof a browser for a single account. While a user can perform the same tasks that an antidetect browser does, it is difficult to switch between different virtual machines. If a user wishes to switch between profiles for social media marketing, an antidetect browser would be more efficient. Its ability to quickly and easily switch between profiles would make it a valuable asset when compared to using a virtual machine.
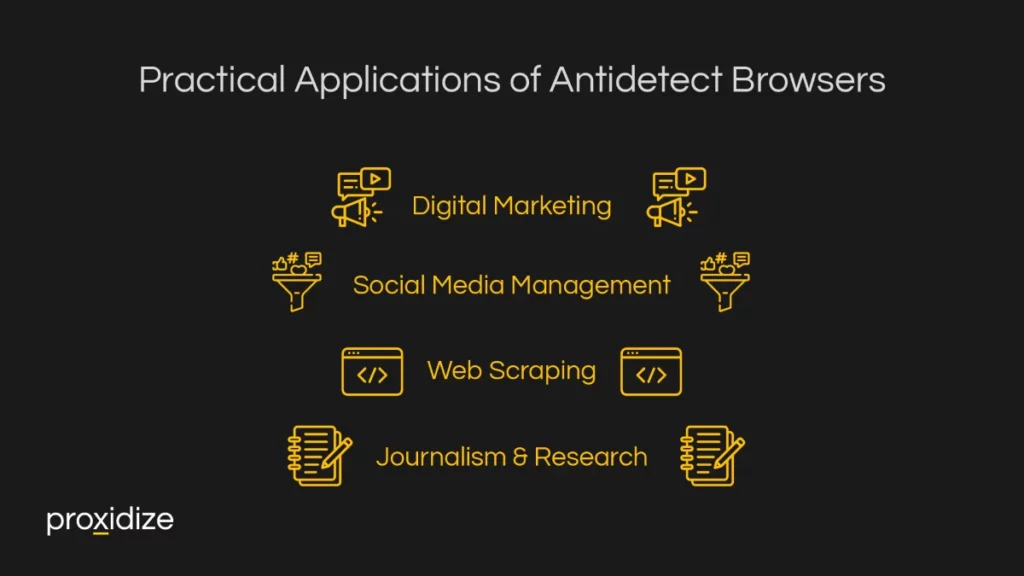
There are numerous practical applications of antidetect browsers. These overwhelmingly make use of the ability to maintain different, isolated profiles. Together with third party tools like CAPTCHA solvers, they can become powerful tools for privacy and automation. Here are just four examples:
Digital Marketing
Marketers and advertisers frequently use anti-detect browsers to manage multiple ad campaigns across different platforms. By using different profiles, marketers are able to keep activities for different clients distinct from one another. By leveraging an anti-detect browser’s geo-spoofing features, marketers can analyze search results and SEO, run ad campaigns, and conduct ad verification, ensuring ads appear in their intended geographic locations.
Social Media Management
Social media management often requires managers to handle several accounts across platforms. Antidetect browsers help them manage these accounts simultaneously from one device, each with a unique browsing environment. By doing this, they can avoid triggering platforms’ limits on the number of accounts one can have. By maintaining isolated profiles, each account’s content feed remains uncontaminated by the other. As an additional layer of protection, each profile can be configured to match the hypothetical device a client is using to use their own social media account.
Web Scraping
Web scraping is the practice of using bots to scrape a website of its data to get any necessary information. Examples include emails for lead generation or prices on e-commerce websites for competitive analysis. By using an antidetect browser while web scraping, one can avoid triggering a website’s anti-scraping mechanisms that can lead to IP blocking or rate-limiting. Many of an antidetect browser’s features offer significant ways to enhance the anonymity needed to do so efficiently.
By spoofing one’s browser fingerprint, a scraper can avoid being blocked on that basis. With proxy integration, they can avoid being identified via their network, and with profile management they can keep each instance of their bot distinct from one another. A lot of antidetect browsers even integrate directly with web scraping tools.
Journalism & Research
Journalists often rely on digital tools to gather information, verify facts, and access diverse sources while maintaining confidentiality and protecting their sources. Antidetect browsers can be valuable tools for them because they help mask their digital identities and locations and allow them to bypass geo-restrictions.
Similarly, academic researchers can use antidetect browsers to access the full breadth of information necessary for comprehensive analysis. By using antidetect browsers, researchers can customize their online experience without content feeds and search results being contaminated by their browsing activities.

There are many antidetect browser suppliers on the market. Each one offers a different combination of features, strengths, weaknesses, and price points. The following is a selection of the most prominent anti-detect browsers on the market:
Antidetect browsers provide essential tools for people seeking enhanced privacy and anonymity online. By employing technologies like browser fingerprinting and spoofing, stealth browsers help mask identifiable information that websites typically use to track users. They allow for deep customization of user agents, screen resolutions, and even time zones to maintain a consistent and untraceable online presence.
Key takeaways from this article are:
Features such as profile management enable users to maintain separate identities for different activities, reducing the risk of cross-contamination between sessions. Whether for personal privacy or professional tasks such as managing multiple social media accounts, antidetect browsers offer a robust solution for navigating the web securely and discreetly. This article has explored how these browsers work and provides an overview of some of the leading options available on the market, providing a foundation for understanding the role they play.
Save Up To 90% on Your Proxies
Discover the world’s first distributed proxy network, which guarantees the best IP quality, reliability and price.
Save Up To 90% on Your Proxies
Discover the world’s first distributed proxy network, which guarantees the best IP quality, reliability and price.
Discount Applied Successfully!
Your savings have been added to the cart.
Looking to get started with Proxidize? Our team is here to help.
“Proxidize has been instrumental in helping our business grow faster than ever over the last 12 months. In short, Proxidize has empowered us to have control over every part of our business, which should be the goal of any successful company.”

By submitting this form, you consent to receive marketing communications from Proxidize regarding our products, services, and events. Your information will be processed in accordance with our Privacy Policy. You may unsubscribe at any time.
RESOURCES
COMMUNITY