What Is Cloudflare Error 1015?
Cloudflare Error 1015 is a specific error message you see on a website protected by Cloudflare when you’ve been rate-limited. In plain terms, it means you sent too many requests too quickly, so Cloudflare blocked further requests from your device for a while. The error page usually says “You are being rate limited” (or a similar error message) and explains that the site’s owner has temporarily banned your IP address due to excessive requests.
This is a protective measure by Cloudflare’s security system, not a bug in the website. It typically happens on Cloudflare-protected websites (sites using Cloudflare’s firewall or anti-bot services) and is meant to safeguard the site from heavy traffic or abuse.
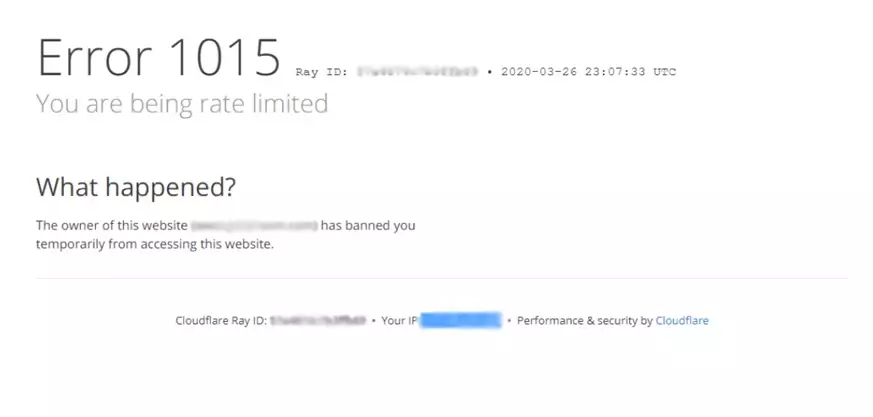
In essence, Error 1015 is Cloudflare’s way of saying “Slow down!” Your browsing or scraping activity crossed the threshold of what the site considers normal. This Cloudflare rate-limiting error is often encountered by web scrapers, automated tools, or even enthusiastic users who refresh pages rapidly. It’s part of Cloudflare’s Web Application Firewall (WAF) and anti-bot system to prevent one client from overloading the server.
In other words, the site is distinguishing your traffic from legitimate users and has flagged it as potentially automated bot traffic or simply too high in volume. Don’t panic — this error is usually temporary, but it does mean you’ll need to change your approach before you can access the site again.
What Is Rate Limiting?
Rate limiting is a technique used by websites and services to control how many requests a single user or client can make within a given time frame. Think of it like a speed limit for web requests: if you exceed a certain number of requests in a short period (for example, X requests per second or per minute), further requests will be blocked or delayed.
The goal is to prevent excessive requests that might abuse the service or overwhelm the server. In practice, most rate-limiting systems track the client’s IP address (or other identifiers) and measure how often requests are coming in. If too many hits occur from the same IP within the set timeframe, the system will intervene — essentially telling that IP “Hey, you’re going too fast, take a break”.
Websites can define rate-limiting rules that specify these thresholds. For instance, a site owner might configure Cloudflare to allow, say, 100 requests per minute from an IP address; on the 101st request within that minute, Cloudflare would trigger the rule and block further requests for a certain duration.
Cloudflare’s infrastructure gives site owners fine control over these parameters, including the time period, the number of requests allowed, and how long to block the client once the limit is exceeded. The block (or “ban”) duration can vary — it could be as short as a few seconds or as long as several hours, depending on the site’s settings.
Often, the ban is temporary (e.g. a few minutes) and will automatically lift once you’ve waited out the period. In more severe configurations, the site might temporarily ban the offending IP for an extended time (Cloudflare allows anywhere from 10 seconds up to 24 hours of ban time in its rate-limiting settings).
Rate limiting is an important defense mechanism on the modern web. It helps stop certain abusive behaviors and attacks — for example, bot attacks like credential stuffing or DDoS (distributed denial of service) floods are mitigated by cutting off clients that make unusually high numbers of requests. It also ensures that legitimate traffic isn’t degraded by a few actors making thousands of requests.
In summary, when you see Cloudflare error 1015, it’s the result of a rate limit rule in action: you hit a predefined limit and Cloudflare has responded by blocking further requests to protect the website.
High-quality scraping and automation starts with high-quality mobile proxies
Why Does Cloudflare Rate Limit Requests?
Cloudflare and site owners enforce rate limits to protect websites from malicious or resource-intensive behaviors. The primary reason is to prevent any single user (or bot) from generating so much traffic that it harms the site’s performance or availability. By cutting off excessive or suspicious traffic, the website stays responsive for other users and avoids potential crashes or slowdowns due to overload.
In Cloudflare’s own words, rate limiting is used to block clients that are “over-using or abusing a web property” and can help stop brute force login attacks, DoS/DDoS attacks, and aggressive web scraping bots. Essentially, it’s a safety throttle to ensure one source of traffic doesn’t overwhelm the site’s infrastructure.
Another major factor is Cloudflare’s anti-bot systems and security algorithms. Cloudflare doesn’t just look at raw request counts; it also analyzes the traffic behavior to distinguish between human users and automated bot traffic. This involves techniques like browser fingerprinting and behavioral analysis.
Cloudflare’s system checks various characteristics of your connection — IP reputation, user agent consistency, JavaScript activity, and even subtle browser traits — to assess how “bot-like” or “human-like” you are. It assigns a kind of trust score (internally, Cloudflare uses a bot score from 1 to 99 to gauge the likelihood a request is from a bot) where a low score means you’re likely a bot. If your requests have a low trust score or exhibit patterns typical of malicious requests (for example, hitting many pages in rapid succession, or skipping resources normal browsers would load), Cloudflare may preemptively rate-limit or block you to protect the site’s integrity. In Cloudflare’s eyes, this is akin to a security guard turning away suspicious behavior to ensure only legitimate traffic gets through.
Cloudflare’s WAF (web application firewall) and bot management tools use traffic behavior analysis extensively. They might challenge a client with captchas or JavaScript puzzles if the traffic seems unusual, and if the client fails these challenges (or is clearly automated), Cloudflare will treat it as hostile. In many cases the response is to serve a 429 “Too Many Requests” or a Cloudflare block page — with Cloudflare, that block often presents as Error 1015 with the message that you are rate-limited.
This is why sometimes even if you didn’t intentionally send hundreds of requests, you might get a 1015 error: Cloudflare’s system decided your browsing pattern or tool is bot-like and clamped down on it for safety. The underlying motive is always to keep the website safe from harm (like scrapers harvesting content too fast, or attackers hammering the site) and to ensure the website’s resources are available to legitimate users who access it in normal ways.
In summary, Cloudflare rate limits requests to prevent abuse, maintain quality of service, and guard against automated threats — it’s about balancing traffic load so that no single source (especially not a malicious one) can negatively impact the site or other visitors.
Common Triggers of Cloudflare Error 1015
What kinds of behavior typically cause a Cloudflare 1015 rate limit error? Here are some common triggers that can lead to this error:
Excessive Scraping or Rapid-Fire Requests
The most straightforward trigger is simply sending too many HTTP requests in a short period of time. This could be a web scraper grabbing pages in quick succession or even a human user furiously refreshing a page.
If you exceed the site’s allowed request rate (for example, hundreds of page fetches within a minute), you’ll likely hit the rate limit wall. Even legitimate actions can trigger this if done in extreme excess — for instance, a user quickly clicking through many pages or an app that pulls data too frequently. Cloudflare monitors the volume of requests per IP and will flag excessive requests as a potential attack or abuse.
Automated Tools and Bots
Using scripts, crawlers, or browser automation libraries (like Python’s requests module, Scrapy, Puppeteer, or Selenium) without precautions can set off Cloudflare’s alarms. Automated bot traffic often performs repetitive actions much faster than a human would, lacking the random pauses and interactions of a real user.
For example, a headless script might load dozens of resources in milliseconds or hammer an API endpoint continuously. Cloudflare’s anti-bot algorithms look for such patterns and will rate-limit clients that behave like bots. In particular, bots that don’t behave like a normal browser — e.g. not loading images or missing certain headers — are easy to identify. If you run a scraper and suddenly see Error 1015, it usually means Cloudflare has detected your activity as automated and too frequent.
Headless Browsers Without Stealth
Many scrapers use headless browsers (Chrome/Firefox in headless mode, via tools like Puppeteer or Selenium) to mimic real user behavior. However, a vanilla headless browser can still be detected by Cloudflare due to subtle fingerprinting giveaways.
For instance, in a regular browser navigator.webdriver is false, but in an unmodified headless browser it’s true — a clear sign of automation. Headless browsers may also lack certain plugins, fonts or have consistent, machine-like timing, which Cloudflare can flag. If you run a headless browser script without a stealth plugin or other evasive measures, Cloudflare’s system can identify the client as a bot and trigger Error 1015. (Developers often use stealth plugins or fortified headless browsers to patch these leaks, making the browser appear more like a real user.)
In short, using a headless browser incorrectly — with default settings — is a common trigger for Cloudflare’s anti-bot rate limiting.
Unusual or Missing Request Headers
Real browsers send a variety of common request headers (user-agent, accept, accept-language, etc.) and handle cookies in typical ways. If your requests are missing typical browser headers or use the exact same header values every time, it can raise a red flag.
For example, a scraper that always uses the same user-agent string and no cookies on every request will stand out. Cloudflare can easily detect when multiple requests come from the same agent or when headers don’t match a legitimate profile.
Similarly, not handling cookies or JavaScript (when the site expects a browser to do so) might lead to a challenge and eventual blocking. Inconsistent or unnatural headers make your traffic fingerprint unique — usually not in a good way. Such anomalies can trigger error 1015 as Cloudflare treats the traffic as a likely bot.
Frequent Page Refreshes or User Actions
You don’t have to be running a scraper to hit the rate limit. If you manually refresh a page over and over in quick succession (or use a browser extension that auto-refreshes pages at a high rate), you can trip the limit.
For instance, users trying to buy limited-release items or checking appointment slots often refresh repeatedly. Cloudflare might interpret this flood of refreshes as a malicious flood and temporarily rate-limit the IP.
Any tool or extension that preloads many resources or opens many connections quickly (like some SEO audit tools or link checkers in a browser) could have a similar effect. The key trigger is the frequency of requests — even if you’re a human, doing things much faster than a typical human user (or doing it from multiple browser tabs in parallel) can resemble bot activity and lead to a Cloudflare 1015 block.
Shared IP or Network Traffic Spikes
In some cases, you might get rate-limited because of collective activity on your network. If you’re on a shared IP address (for example, at an office, university, or using a VPN exit node that many people use), all those requests from different users are seen as coming from one IP by Cloudflare. This aggregate can exceed the limit.
For instance, imagine 50 people in a company all accessing a Cloudflare-protected site around the same time — the burst from one IP could look like a single client making dozens of requests and trigger a block. Likewise, if you run multiple scraping processes in parallel on one server/IP, their combined request rate could push you over the threshold.
Cloudflare’s rate limiting is often per IP, so high traffic load from one IP (even if it’s “legitimate” load spread across users) can cause everyone on that IP to see error 1015.
Using Known Proxy/VPN IPs
Paradoxically, using proxies is a solution to avoid rate limits (as we’ll discuss), but using the wrong proxies can cause rate limiting instantly. Cloudflare maintains intelligence on IP reputation. If you connect from a data center IP range or a well-known VPN exit, Cloudflare might treat that IP with suspicion (such IPs often correlate with scrapers and attacks). In fact, some Cloudflare configurations will challenge or rate-limit VPN/proxy connections by default.
So, if you are browsing or scraping via a cheap public proxy or VPN and you see Cloudflare Error 1015, it could be that the IP itself was flagged as untrusted. Essentially, the site may have lower tolerance for that IP, causing you to hit a stricter rate limit or immediate block. This is why many scrapers prefer residential proxies or high-quality proxy networks — they carry higher trust and won’t trigger Cloudflare simply by virtue of their IP identity.
These are typical scenarios that lead to Cloudflare’s 1015 rate-limit error. In summary, anything that makes your traffic look like a high-volume or non-human pattern — be it fast scraping, unmodified headless browsers, or repetitive requests — can trigger the site’s rate limiting. Knowing these triggers can help you diagnose why you got blocked and avoid similar patterns in the future.
How to Resolve Cloudflare Error 1015
Finding yourself face-to-face with an Error 1015 page can be frustrating, but there are several steps you can take to resolve it. Here’s how you can get back on track:
1. Stop or Slow Down Your Requests
The first and most important step is to immediately pause the activity that caused the rate limit. If you were running a script or rapidly refreshing, stop doing so. Often the ban is temporary, so simply waiting can solve the issue.
Give it a few minutes (or longer, depending on the severity of the limit) before trying again. This cooldown period allows the rate limit counters to reset. In many cases, Error 1015 will disappear on its own once the timeframe of the rate-limit rule has passed. Think of it as waiting for a traffic light to turn green after speeding — patience is key.
2. Reduce Your Request Frequency
When you retry, do so at a much slower pace. Manually, that means don’t hit refresh repeatedly; if you’re a human user, try to browse normally. If you’re running an automated task, throttle your program to send requests at a reasonable interval instead of back-to-back.
For example, if you were making 20 requests per second, cut it down to 1 request every few seconds and see if the error abates. Essentially, you want to come back under the radar of the site’s rate limits.
Implementing a delay between requests or using incremental backoff (waiting longer after each failed attempt) can quickly get you out of the penalty box. Once your traffic looks more like legitimate user activity, Cloudflare will likely allow it to proceed.
3. Change or Rotate Your IP Address
If waiting isn’t an option or the ban persists, you may attempt to access the site from a different IP. For an individual user, this could mean switching networks (for instance, try using your mobile network instead of your Wi-Fi, or vice versa) or restarting your router if you have a dynamic IP that changes.
For web scrapers, this means using a proxy. A simple fix is to route your requests through a proxy server or VPN to present a new IP to the website. However, remember the note above: not all proxies are equal. It’s best to use a reputable proxy pool or residential proxies that aren’t already flagged by Cloudflare Services exist that provide rotating proxies so that each request can go out from a different IP address, effectively diluting the volume per IP and bypassing the rate limit.
By assigning a unique proxy IP for each request, you make it appear as if many different visitors are browsing, avoiding Cloudflare’s one-IP rate threshold. The key here is “anonymizing” or distributing your traffic. If you go this route, proceed carefully: use proxies that have a good IP reputation (Cloudflare’s trust score for the IP should be high) to avoid immediate blocks due to the proxy itself.
4. Double-Check Your Tools and Headers
If you suspect you were flagged as a bot, try accessing the site in a regular browser (with JavaScript and images enabled) to confirm that you’re not generally banned. Often, you’ll find you can load the site in a normal browser but not with your script — a sign that it was your automation’s fingerprint that got it blocked.
In that case, adjust your tool’s settings: for example, set a realistic user-agent string (pretending to be Chrome/Firefox instead of a blank or default agent) and include typical headers like Accept-Language. Enable cookie handling in your script so you retain any session cookies (Cloudflare might require a cookie challenge solution).
By making your requests look more like those from a normal browser, you may regain access. In short, polish your request profile to appear legitimate. If you were using a headless browser, consider adding a stealth plugin or using an “undetected” mode so it no longer trips the bot detectors. These tweaks can resolve the block when you try again, because Cloudflare will see a more normal traffic pattern.
By following these steps, you should be able to recover from an error 1015 situation. In many cases, simply slowing down and waiting is enough. In more stubborn cases, switching IPs or refining your request behavior will do the trick.
Once you regain access, it’s important to learn from the experience and adjust how you interact with the site to avoid getting rate-limited again. The next section covers exactly that: preventing a repeat of Error 1015 in the future.
How to Avoid Getting Rate Limited in the Future
Prevention is better than cure. To avoid encountering Cloudflare Error 1015 again, you’ll want to adopt strategies that keep your traffic under the radar and respect the site’s limits. Here are some tips to help ensure you don’t get rate-limited moving forward:
Throttle Your Request Rate
The simplest way to not hit a rate limit is to send requests at a moderate pace. Build rate limiting into your own script or behavior — for example, if you suspect the site might allow ~50 requests per minute, aim for significantly less than that.
Introduce deliberate delays between requests. A good practice is to add randomness: instead of a fixed 1-second interval, use 1–3 seconds (randomly) between requests, so your pattern is less robotic. If you receive a 429 or 1015 response, implement an exponential backoff (wait a bit, then try, if blocked again wait even longer). This mimics how a real user might slow down when a site is unresponsive.
Throttling your scraper’s speed not only prevents triggering Cloudflare’s limits but also is kinder to the website’s server (an aspect of ethical automation). Remember, consistency in high-frequency hits is what gets noticed; slowing down keeps you in the realm of legitimate traffic.
Use Rotating Proxies or a Proxy Pool
If you need to make a lot of requests (for example, crawling a large site), consider distributing those requests across multiple IP addresses. Using a proxy pool is an effective way to avoid any single IP getting rate-limited.
For best results, use high quality proxies. Mobile proxies are a good example — they source their IP addresses from mobile carriers, so Cloudflare is less likely to distrust them compared to cheap or low-quality alternatives.
Rotate your IP frequently — many scraping setups assign a new IP for each request or each batch of requests. This way, even if you make 1,000 requests, each IP might only make a handful, staying well below the radar.
Some advanced proxy services offer self-healing proxies, meaning if an IP gets blocked or flagged, the service automatically replaces it with a new one, maintaining a smooth operation. By leveraging a broad proxy network, you can avoid frequent rate limits because no single IP or identity is doing “too much” from Cloudflare’s perspective.
Mimic Real Browser Behavior
The more your automated traffic looks like a normal web browser, the less likely Cloudflare’s anti-bot systems will single you out. This means enabling JavaScript (if possible) or using a headless browser for complex sites, handling cookies, and sending all the headers a regular browser would.
Use up-to-date browser automation libraries that support stealth: for instance, Puppeteer with a stealth plugin, or Selenium with tools like undetected-chromedriver. These tools suppress the obvious tell-tale signs of automation (like navigator.webdriver and other headless browser fingerprints) and can rotate or mask other identifiers.
Also, vary your browser headers and metadata. Cloudflare can compare things like User-Agent, Accept-Language, and even modern Chrome’s client hints headers. Ensure that if you pretend to be, say, Chrome on Windows, the other headers (and TLS fingerprint, if possible) align with that profile.
Many scrapers fail because they send conflicting information (e.g., a mobile User-Agent but headers that a mobile browser wouldn’t send). Use a browser fingerprint tool or service to test your requests and see how “real” they look — this can help you adjust your script to better blend in. The goal is to emulate normal browsers and human browsing patterns as closely as you can.
Rotate Identifiers
In addition to rotating IPs, rotate other identifiers that Cloudflare might use to track you. For example, prepare a list of legitimate User-Agent strings (covering different browsers and devices) and randomize which one you send with each request. But crucially, make sure the rest of your request is consistent with that User-Agent (as noted above). You can also rotate other headers like the “Accept” order or add plausible variations in “Accept-Language”.
Some scrapers even randomize minor aspects of the TLS handshake or HTTP/2 settings via advanced libraries to avoid a fixed fingerprint. Moreover, handle cookies properly: if Cloudflare sets a cookie after a challenge (like __cfduid or others), reuse that cookie on subsequent requests rather than starting fresh each time. This shows continuity like a normal session.
By rotating headers and other fingerprinting data in a coordinated way, you make each request look potentially like a new legitimate user, which makes it much harder for Cloudflare to label your traffic as a single abusive bot. Just rotating IP alone is good, but combining it with varied headers and agents is even better for stealth.
Choose Tools/Providers with Anti-Bot in Mind
If you’re using third-party services or providers for scraping, pick ones known for proxy unblocker capabilities or anti-bot expertise. There are “scraping APIs” offered by companies (including Cloudflare themselves and others) that handle the heavy lifting of bypassing bot protections. These services will manage IP rotation or allow you to specify your own rotation intervals, solve Cloudflare challenges, and present realistic browser fingerprints for you.
If coding your own solution, stay updated on anti-bot techniques: the community often shares methods to bypass Cloudflare’s latest hurdles (for example, updates to Puppeteer stealth or new libraries that can solve Cloudflare’s JavaScript challenges). In summary, use the right tools for the job — those designed to simulate human users and avoid detection.
Monitor and Adjust in Real-Time
Make your automation smart. Implement checks for response codes like 429 or the presence of Cloudflare challenge pages so that if you start getting near the limit, your system can slow down automatically.
For example, if you suddenly get a Cloudflare interstitial or a couple of 503/1015 responses, have your scraper back off or switch proxies before a full block happens. This kind of self-healing logic can prevent minor rate-limit warnings from turning into full-blown bans.
Keep an eye on your scraping logs — if you notice responses taking longer or partial data (Cloudflare sometimes serves a “challenge” page with a 5-second delay), those are signs to ease up. By being responsive to Cloudflare’s signals, you can stay just below the threshold that would trigger an error. Over time, you may even discover the site’s approximate rate limits and pattern detection, which lets you fine-tune your crawl speed to a safe level.
By following these practices, you significantly reduce the chance of triggering Cloudflare’s rate limits. Essentially, respect the website’s boundaries: fetch data at a reasonable pace, distribute your requests, and make your automation as well-behaved as possible. Not only will this help you avoid errors, but it’s also the polite way to scrape — minimizing impact on the site and blending in with legitimate user traffic.
Best Practices for Sustainable Automation
Beyond just avoiding errors, it’s important to consider the ethics and sustainability of your web automation or scraping efforts. Adopting best practices for ethical and sustainable automation will not only prevent errors like 1015, but also ensure you’re not causing harm to the websites you interact with. This includes straightforward steps like:
- Respect the Website’s Usage Policies: Always review the website’s Terms of Service or robots.txt file to understand their stance on automated access. If a site explicitly forbids scraping or has an API for data access, it’s best to follow those rules. Ethical automation means playing by the rules set by the content owner.
- Don’t Overload the Server: Scrape or automate tasks in a way that doesn’t put undue strain on the website. This ties in with rate limiting — even if Cloudflare would let you make 1,000 requests, think about the load you’re placing on the site. Be a good citizen: Targeted data collection is better than fetching everything blindly.
- Implement Your Own Rate Limits and Throttling: We mentioned this in avoidance, but it’s worth emphasizing as an ethical practice. By throttling your bot, you demonstrate respect for the site’s resources.
- Use Data Responsibly and Respect Privacy: This goes slightly beyond Cloudflare, but important ethically. If your automation involves user data or anything sensitive, handle it with care and in compliance with privacy laws. Do not scrape personal information that is not meant to be public, and certainly do not use automation for any malicious purposes (like trying to break into accounts or spam).
- Stay Informed and Adapt: The landscape of anti-bot technology (including Cloudflare’s techniques) evolves continuously. What works today to bypass or avoid rate limits might not work tomorrow if Cloudflare improves their bot detection. Make it a practice to stay updated with the community — forums, blogs, and documentation — for any changes.
By adhering to these best practices, you ensure that your use of automation or web scraping is both effective in the long run and respectful to the ecosystem. You’ll have fewer interruptions (like Cloudflare Error 1015) because you’re working with the system’s limits, not against them.
Ultimately, successful automation is about balancing your goals with the stability and rules of the target site — doing so will keep your projects running smoothly and maintain a positive relationship (even if implicitly) with the websites you interact with.
Conclusion
Cloudflare Error 1015 is triggered when a user triggers a website’s rate-limiting mechanism, which exists to protect websites from excessive requests, whether from automated scrapers or overly enthusiastic users. To resolve error 1015, pause your activity and let the temporary ban reset. Next, you need to adjust the frequency of your requests (from the same IP), whether that’s refreshing less often, slowing your scraper down, or rotating through your proxies more often.
Understanding Cloudflare’s detection mechanisms and why you were rate limited to begin with is important. The system analyzes factors such as browser fingerprints, behavior patterns, and common request headers to sort between human users and automated bots. By studying these methods, you can tailor your approach to avoid triggering the rate-limiting rules.
Key Takeaways:
- Rate limiting prevents websites from being overwhelmed with requests.
- Cloudflare tracks not just the number of requests but browser fingerprints and request patterns.
- Implementing delayed requests with randomized intervals significantly reduces triggering rate limits.
- Rotating through different proxies and request identifiers can make the traffic you generate look more legitimate and less “bot-like”.
- Mimicking authentic browser behavior by handling cookies and maintaining consistent header profiles improves request acceptance rates.
Prevention strategies that respect website boundaries while implementing technical countermeasures represent the most sustainable approach to navigating Cloudflare’s protective ecosystem. Ethical automation practices ultimately benefit both users and web infrastructure integrity.
Frequently Asked Questions
What causes Cloudflare Error Code 1010?
Cloudflare Error Code 1010 occurs when a website’s security system identifies your browser’s signature as suspicious or banned. This can happen due to the use of automated tools, headless browsers, or certain browser extensions that modify your browsing profile.
How can I fix Cloudflare Error 1010 as a website visitor?
Try switching to a different browser, disabling browser extensions, disconnecting from VPN or proxy services, and clearing your browser’s cache and cookies. If the issue persists, contact the website owner for assistance.
What can website owners do to resolve Error 1010 for their visitors?
Website owners can review and adjust their Cloudflare settings, such as disabling the Browser Integrity Check, whitelisting trusted IP addresses, or creating custom configuration rules to allow specific user agents while maintaining overall protection.
Are there advanced solutions for persistent Cloudflare Error code 1010 issues?
Yes, advanced solutions include creating custom configuration rules, modifying request headers, addressing reverse proxy challenges, and using alternative automation approaches like cloud-based fortified browsers designed to bypass fingerprinting.
How can I prevent Cloudflare Error code 1010 in the future?
To prevent future occurrences, website owners can implement targeted exception rules and adjust Browser Integrity Check settings. Visitors and automation users can fortify headless browsers, implement proper header rotation, mimic authentic browsing patterns, and consider using specialized proxy solutions like mobile proxies.