What do you do when you need every packet that leaves your iPhone or iPad to pass through a proxy, yet the network you are on blocks or throttles traditional VPN tunnels?
An unfamiliar scenario for many, but for those relying on hostile public Wi‑Fi, corporate firewalls, or regional censorship it’s often the only alternative that still gives them full control over where their traffic exits. Shadowrocket, an iOS‑only, rule‑based proxy client, fills that gap by applying granular routing policies at the operating‑system level.

How Shadowrocket Works
Shadowrocket is built on Apple’s Network Extension framework. The app inserts a local “tunnel” interface between iOS and the wider network stack, giving it visibility into every TCP, UDP, and DNS request your device generates. Because Apple restricts packet‑tunnel entitlements to apps that implement their own VPN or proxy logic, Shadowrocket would not function unless it were built on this framework.
Unlike a blanket VPN, which could offer you split tunneling with a basic IP routing table, i.e. “10.0.0.0/8 → VPN, everything else → Internet,” Shadowrocket acts more like a programmable firewall plus multi‑proxy router, where one rule can say “*.doubleclick.net via rotating mobile proxy,” the next “netflix.com direct,” and a third “block *.tracker.example.”
The rule engine accepts multiple match types — domain keyword, suffix, full host, CIDR, or GeoIP. Once you set your rules, a “first match wins” model evaluates each outbound connection against your rule list in top‑to‑bottom order. The first rule that matches hands the request to the proxy label you named; if nothing matches, a “FINAL, DIRECT” rule usually lets the traffic exit unproxied. This approach means YouTube can stream on a fast home connection while ad‑tech domains or a QA test site simultaneously tunnel through a rotating mobile IP.

Installing and Configuring Shadowrocket
Begin by purchasing Shadowrocket from the App Store (currently USD $2–4 depending on region). On first launch, the app asks for permission to add a VPN profile; this profile is not a VPN in the traditional sense but gives Shadowrocket kernel‑level authority to create its virtual tunnel interface. Granting that permission is mandatory — without it the app cannot intercept traffic.
Once installed, you’ll see the home screen, which shows whether you’re connected, where you can see your global routing config, a way to test your connectivity, and a way to add a new server.
Adding a new server is easy. From the Add Server screen you can add the address, port, and credentials of your proxy server, along with other options.
When setting the server type, you’ll have a lot of options to choose from.
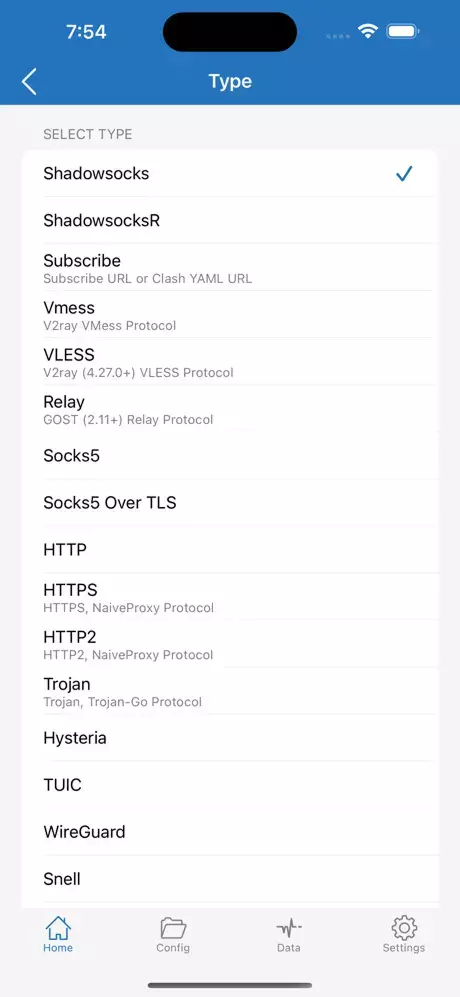
Remember that the type you choose must match whatever is running on the exit server; otherwise the handshake will fail and Shadowrocket will show “unavailable” or endless reconnection attempts.
| Type | How It Moves Traffic |
|---|---|
| Shadowsocks | Encrypts TCP & UDP in its own lightweight framing; usually on port 8388 or any high port. |
| ShadowsocksR | Same as above plus custom “obfs” layers (auth_sha1_v4, tls1.2_ticket_auth, etc.) |
| Subscribe | Shadowrocket downloads a subscription file that may contain dozens of nodes of any type. |
| Vmess | Multiplexed TCP (optionally UDP) wrapped in JSON frames; can be disguised under WebSocket, gRPC or TLS |
| VLESS | Same framing options as VMess but relies on outer TLS/XTLS for encryption |
| Relay | Acts like a layer‑4 forwarder or “hop” between other proxies |
| Socks5 | Transparent TCP and UDP relay, no encryption by default |
| Socks5 Over TLS | Same SOCKS5 semantics wrapped in a TLS tunnel (port 443 or 8443) |
| HTTP | TCP only, no built‑in encryption |
| HTTPS | Encapsulates traffic in HTTP/2 or HTTP/3 requests that look like Chrome browsing to a regular website |
| HTTP2 | Same stealth idea but restricted to H2 (TCP). |
| Trojan | Raw or WebSocket‑wrapped data inside a genuine TLS session to a real domain with valid certificate |
| Hysteria | Uses UDP 443; includes NAT traversal and obfs |
| TUIC | UDP 443; more efficient than Hysteria on short flows |
| WireGuard | Kernel‑level UDP tunnel, ChaCha20‑Poly1305 encryption |
| Snell | TLS‑based, with per‑session PSK, UDP pass‑through, simple congestion control |
You can also pick between a variety of different plugins, extra transport wrappers that sit between the core proxy protocol. (for example, Shadowsocks) and the network.
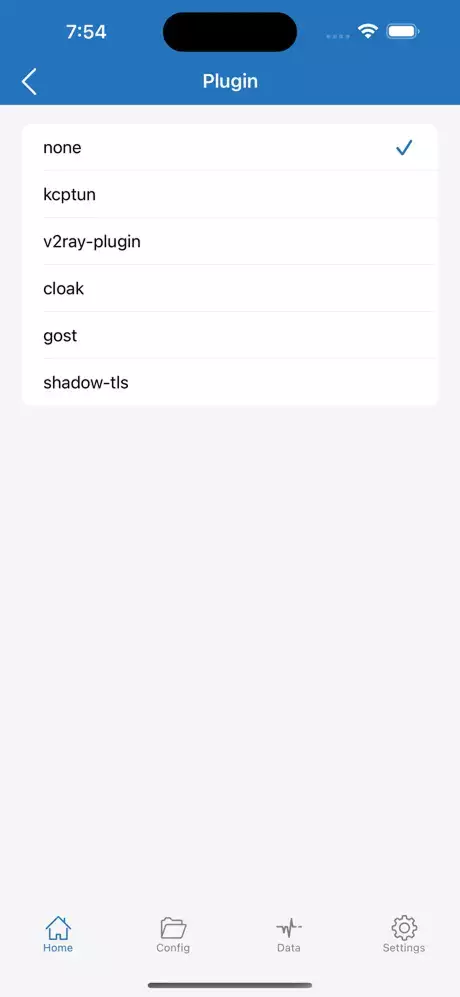
| Plugin | How It Works |
|---|---|
| none (default) | — |
| kcptun | Bundles, compresses and forward‑error‑corrects multiple TCP segments inside a single UDP stream, with selective ACKs and configurable FEC redundancy. |
| v2ray‑plugin | Wraps traffic inside WebSocket or HTTP/2/HTTP/3 sessions and can add TLS; to DPI it looks like normal browser traffic to a CDN. |
| cloak | Performs a full, valid TLS handshake to a “front” domain and keeps sending padding frames so packet sizes match genuine web browsing. |
| gost | Shadowrocket passes data to a local GOST stub, which then negotiates the chosen wrapper with the server‑side GOST. |
| shadow‑tls | Sends a legitimate TLS ClientHello and part of the handshake to a decoy domain, then switches to an encrypted inner stream while keeping the outer TLS session alive. |
Every plugin must be running both on the client (Shadowrocket) and on the exit server. If the provider does not offer matching server‑side support, choosing a plugin will break the connection.
Beware Fake Shadowrocket Sites and APKs
The only legitimate Shadowrocket build is the iOS version sold on Apple’s App Store. The developer reiterated on X (formerly Twitter) in December 2022 that “Shadowrocket has not yet created an official website. Anyone claiming to be the official website of Shadowrocket must be a scammer.”
Despite that statement, numerous look‑alike domains — such as ShadowrocketVPN, Shadowrocket for Android, and ShadowrocketDownload — use the same logo to distribute questionable APKs or subscriptions with no link to the genuine iOS client. For safety, obtain the app only through Apple’s App Store listing published by developer Shadow Launch Technology Limited.

Shadowrocket Use Cases
A common scenario is geo‑locked media. Streaming platforms often restrict libraries by both country and network type; a mobile ASN in the target market can unlock content that a datacenter VPN cannot. By assigning a GeoIP, US, MobileProxy rule — the United States in this example — you ensure only U.S.‑bound traffic uses your mobile proxy node, while everything else goes direct.
Developers and QA teams use Shadowrocket for device‑level A/B testing. For example, a Chinese iOS‑testing tutorial shows Shadowrocket configured as a VPN‑style packet tunnel so that any app — even those that ignore the normal Wi‑Fi proxy setting — has its traffic forced through Burp Suite for inspection.
Because the utility captures traffic from every app — native or web — it reveals how ad SDKs, payment gateways, or API calls behave when seen as coming from a specific carrier IP block. In advertising compliance work, auditors run Shadowrocket profiles that pipe only ad‑tech domains through carrier proxies while leaving analytics or billing endpoints untouched, producing clean measurement datasets.
As a result, you can technically use Shadowrocket as an adblocker, allowing regular website content to pass through while outright blocking traffic from ad sites.
Verifying the Setup
Shadowrocket offers two quick diagnostics. First, tap Connectivity Test next to your proxy label; the tool measures round‑trip time and reports success or failure. A consistent latency value indicates authentication succeeded and the endpoint is reachable.
Second, open a browser (Safari or any installed app) and visit an IP‑echo service like ifconfig.me. With Shadowrocket off, the site should show your real ISP address; with it on and a rule triggered, the displayed IP should now match the Proxidize node.
For more granular confirmation, browse to a domain covered by a specific rule and then inspect Data → Connections inside Shadowrocket. You will see the host, the rule name that matched, and the proxy label in use. If the wrong rule fires, drag your intended rule higher in the list; order is significant.
Limitations and Operational Considerations
Shadowrocket cannot force‑proxy QUIC traffic (UDP 443) if the destination site refuses to downgrade to HTTP/1.1 or HTTP/2. As a workaround, some users block UDP or employ server‑side rules that force a TCP fallback. Similarly, certain system services — like Apple Push Notification — may bypass third‑party tunnels by design; test critical workflows before assuming 100% coverage.
Running a persistent tunnel plus detailed logging can increase battery drain by 10–20% on older devices. Disabling packet capture and limiting rule complexity mitigates the impact. Finally, always confirm that routing commercial scraping traffic through mobile ASNs complies with both your local telecom regulations and the target site’s terms of service; legal exposure varies by jurisdiction.
Conclusion
Shadowrocket offers a flexible, rule‑driven alternative to monolithic VPNs for iOS. By intercepting traffic at the OS layer and applying match‑based routing, it gives security professionals, marketers, and QA teams a way to direct only the traffic that matters through specialised exit nodes while everything else stays local for speed and stability.
Key Takeaways:
- Shadowrocket routes iOS traffic by matching each request against user‑defined rules, not by tunnelling everything through a single VPN.
- Adding Proxidize proxies is straightforward.
- Verification is essential: use Shadowrocket’s own Connectivity Test plus an external IP‑echo site to confirm that specific domains exit through the intended mobile or residential IP.
- Be aware of limitations such as QUIC flows and additional battery consumption, and verify that your use of mobile ASNs complies with local regulations.
Proper configuration boils down to three repeatable steps: import or create the proxy, write clear rules, and verify those rules with built‑in tests and third‑party IP‑echo sites.




