Forward proxies are a way to mediate outgoing traffic and centralize the traffic leaving and entering the network. In this article, we’ll explore what forward proxies are, how they fit into your corporate network, and the benefits they offer.
What Is a Forward Proxy?
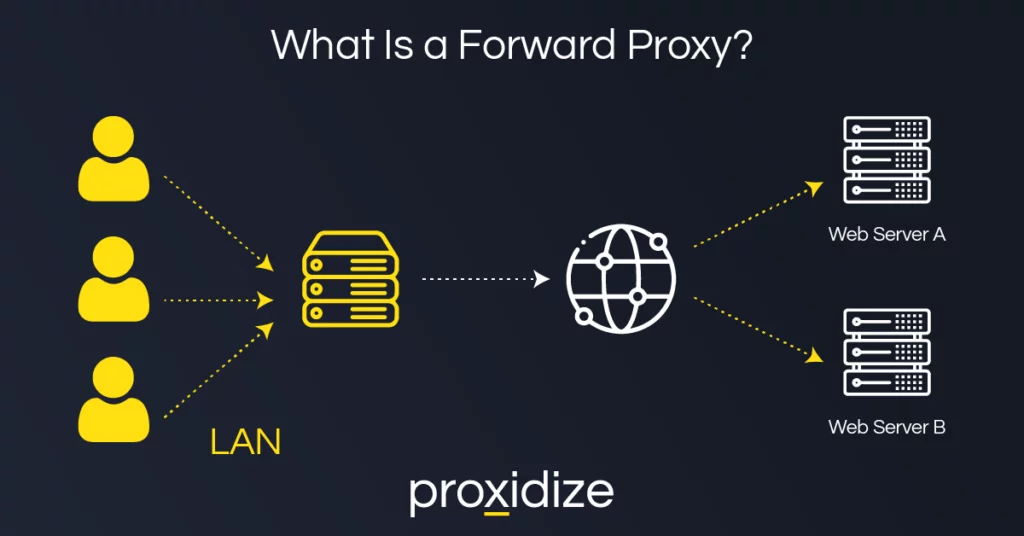
You may have several devices on the internal network that want to reach a public internet resource. Instead of letting each machine’s real IP address reach out to the internet, a forward proxy server stands at the network perimeter and fronts those client requests. Essentially, it’s an intermediary server that routes outbound traffic on behalf of your internal users.
This isn’t to be confused with a reverse proxy server, which deals with incoming traffic heading toward origin servers. Forward proxies push data out. When an individual user inside your private network attempts to access an external server (like an e-commerce site or a repository on the public internet), the forward proxy intercepts that traffic to fulfill the requests from clients.
Because these requests are funneled through a single server, admins can create a single set of security policies, enabling everything from content filtering to malicious domain blocking. You’ll often see a forward proxy used in tandem with a traditional firewall, providing an additional layer of defense while controlling how and when your internal machines talk to the outside world.
How Does a Forward Proxy Work?
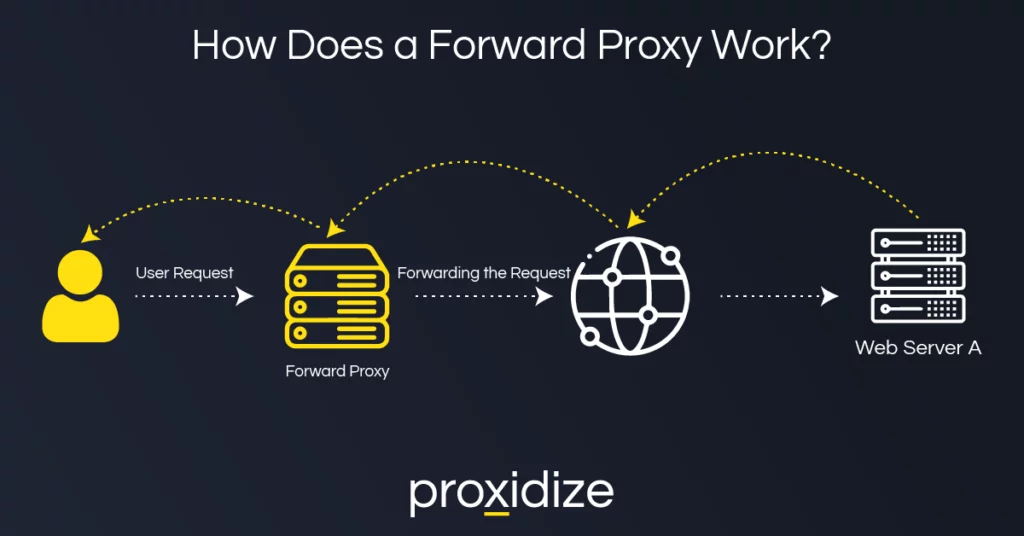
Let’s explore how a forward proxy works in practice. First, someone in your internal network tries to visit a website or download something. That request never leaves the user’s machine unfiltered. Instead, the request goes through proxy settings — maybe via a dialog box or a proxy auto-configuration (PAC) file.
The forward proxy sees this request, checks it against predefined rules or access policy items (for instance, “Block known malicious websites,” “Deny access to phishing sites,” or “Limit access to resources by certain users”). If everything checks out, the proxy makes the request on behalf of the user, fetches the content, and returns it.
Because the forward proxy masks client IP addresses from the destination server, it can boost user anonymity for your internal users. The public-facing servers on the internet see only the proxy’s IP, sparing your employees from revealing their physical location or corporate network architecture. Meanwhile, you can track usage, spot potential attack methods, and maybe even block a suspicious outbound connection to a malicious website.
Types of Forward Proxy
There are a few different types of forward proxy servers. Let’s walk through a few of them:
1. Traditional On-Premises Forward Proxies
These might be dedicated forward proxy solutions physically sitting in your server room. They enforce policies such as content filtering rules, scan traffic for threats, and handle proxy functionality for your whole corporate network.
2. Cloud-Based Forward Proxies
Cloud-based forward proxies offer an off-premises solution that can be scaled without taking up physical space. IT teams can update configuration files and manage policies from an administrative user interface, so there’s no need to handle everything in a local data center.
3. SSL Forward Proxy
An SSL forward proxy allows you to decrypt and re-encrypt SSL/TLS traffic. If you want to check for malicious content or apply content rewriting to enforce certain guidelines, these specialized proxies can do the job — though you’ll need to be mindful of privacy laws and user consent.
4. Residential Proxies
Offered frequently by third-party proxy server providers, residential proxies use IPs assigned by residential ISPs (the kind you have at home). Websites see an IP that looks like it comes from an ordinary user machine. This can be helpful for tasks like web scraping, though it’s not always the top pick for internal corporate use.
Why Use a Forward Proxy?
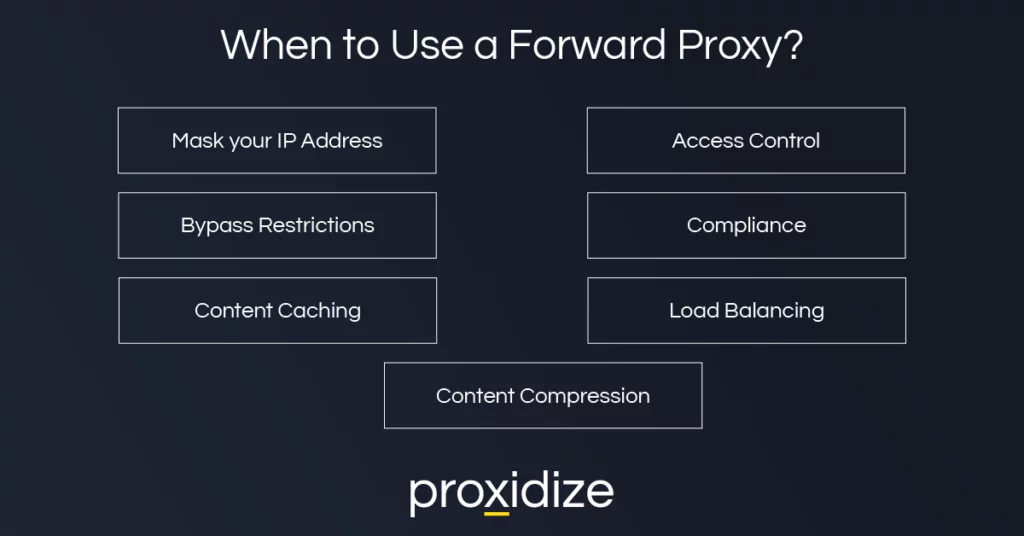
Next question: Why go through the trouble? For businesses and other organizations of a certain size, a forward proxy offers them the opportunity to manage their outgoing traffic in a few interesting ways:
Policy Enforcement
Forward proxy servers let you apply a unified set of access control policies. By funneling outbound traffic through a single server, you get to enforce predefined rules — like blocking inappropriate content, allowing access to certain social media sites only during lunch breaks, or restricting content categories that represent a higher risk. The proxy ensures policy enforcement for all requests from clients in one fell swoop.
User Privacy Protection
A forward proxy adds an additional layer of privacy to all the network’s users, regardless of whether the proxy is intended as an anonymizing tool or not.
Traffic Visibility
On top of preventing every website from seeing your entire corporate setup, forward proxies also let you keep an eye on what your client traffic is doing. Every request from your internal machines is logged, scanned for harmful content, and can be studied to detect shadow IT. For example, if your team is hypothetically pushing data to an unvetted “free file-sharing site,” you can catch that. If certain employees are using a software agent you never approved, the forward proxy might flag it.
Shadow IT
The term shadow IT refers to the unauthorized introduction of network resources or tools by employees without official permission. If you don’t have a forward proxy, these hidden apps can slip under the radar. With a forward proxy in place, there’s no sneaking outside the standard channels — every outbound traffic request follows a strict path. It offers you the opportunity to quickly stop or investigate suspicious activity or misconfigured remote server addresses.
Conclusion
For organizations or networks of a certain size, forward proxy servers act as a gateway to the outside world that internal server traffic has to pass through to reach the internet. By controlling outbound connections at a single point, you can reduce your attack surface and implement consistent network policies.
Key takeaways from this article:
- Forward proxies offer a central checkpoint for policy enforcement — blocking undesirable websites, applying content filtering rules, and scanning traffic for threats.
- They maintain user anonymity by masking real IP addresses and substituting an additional public IP address instead.
- They create traffic visibility that helps spot shadow IT and suspicious access patterns.
- They work seamlessly alongside other network security tools, like firewalls.
- They can be as simple as a single on-prem device or scaled up as cloud-based forward proxies, making them easy to adapt to various network configurations.
In short, if your organization cares about controlling outbound requests, guaranteeing user privacy for your employees, and locking down your internal resources from scrutiny, consider a forward proxy.