Many of our articles about proxy servers that function as anonymizing technology. Many of them also have other uses as well, but all of them are servers that for one reason or another intercept outgoing requests and forward incoming responses to the client. Log proxies are an exception, as not only are they not anonymizing software, but they don’t even sit between client and server.
Log proxies are servers that operate alongside whatever network system they’re a part of to aggregate the logs of any device that generates them. They’re an important cog in the machinery of any network, collecting the logs of events that have already occurred. They’re able to add timestamps to them, redact irrelevant or sensitive information, and even format that information in a way that is useful upstream. They then forward that information to a larger aggregation server that pools data from multiple log proxies.
In this article we’ll explain what log proxies are, what role they play in network management, and how they differ from the proxies we usually discuss.
What Is a Log Proxy?
A log proxy, also known as a log forwarder and logging agent, is a component that collects log data from devices and applications and forwards them on to their final destination. Instead of operating within the flow of data traffic — like the other proxy servers we’ve discussed — a log proxy specializes in receiving logs of events, metrics, and more from various services. They’re the first point at which log data is aggregated from multiple sources.
A log proxy intercepts log streams from a variety of sources including microservices, containers, and virtual machines. Once collected, it can perform different operations. Beyond aggregating the data, it can filter out information or collect only a sample. It can also enrich and transform the data by adding metadata including timestamps and host info or removing sensitive information. A log forwarder can send the data to one or more destinations such as backend servers for additional processing.
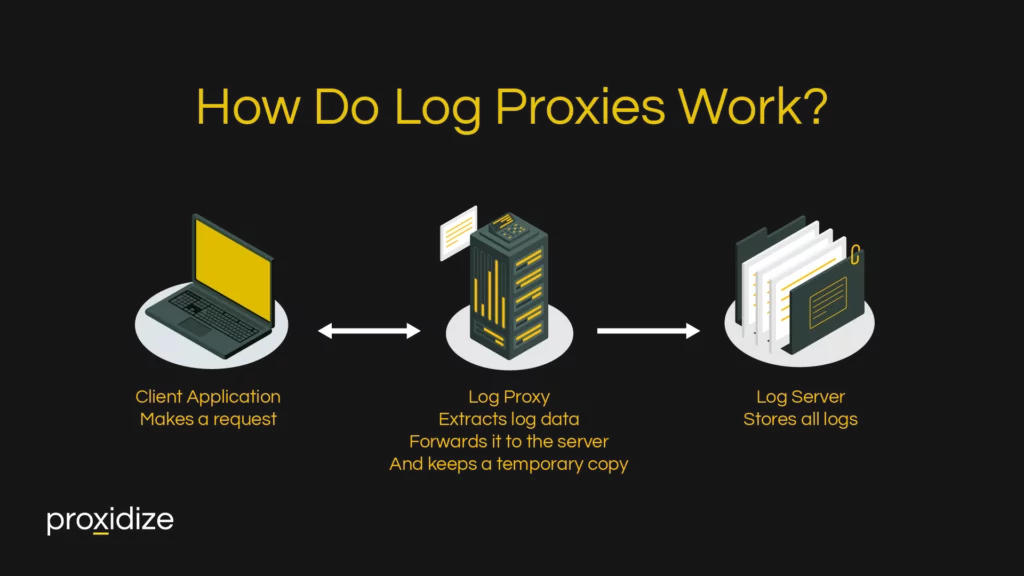
How Does a Log Proxy Work?
The log data that is collected is not real-time and is only collected once the event being logged has already occurred. Unlike other proxies, a log proxy doesn’t sit directly in the chain of traffic but sits out of band, which is to say it forms part of a log collection network rather. A log proxy doesn’t intercept any live user data and concerns itself only with processing log data.
In a centralized logging system, log proxies are often the first point of aggregation. By installing a log proxy (or agent) on each host or node, you ensure that logs from all those containers, applications, or microservices flow to one place. This makes troubleshooting easier, as the logs of the problem area can be conveniently pulled up.
Log proxies not only aggregate information, but can transform and enrich data. For example, if your application emits logs in plain text, a log proxy could standardize that output into JSON, add host or container metadata, and redact any sensitive fields (e.g., user passwords). This makes subsequent filtering, alerting, and analysis far more reliable. In short, rather than dealing with a dozen logging formats, you can converge on one clean, consistent format.
Another benefit of using a log proxy is in the event of a network glitch. A log proxy can keep logs in a short-term buffer — often either in memory or on disk. Once the downstream problem has been solved, the log proxy resumes sending.
Use Cases and Deployment Context
Microservices & Containers
If you’re running Kubernetes or Docker, you know microservices can spin up and tear down in seconds. A log proxy on each node automatically captures logs from each container, so you don’t lose crucial debugging info when a container disappears. This is especially valuable in large clusters, preventing a messy scramble to locate log files.
DevOps & SRE
DevOps and SRE teams thrive on continuous monitoring, rapid feedback, and swift troubleshooting. Log proxies facilitate this by:
- Alerting teams to error patterns across the environment.
- Correlating logs from multiple microservices in one console.
- Automating the process of shipping logs to analytics platforms like Elasticsearch or Splunk.
Security & Compliance
From PCI-DSS to GDPR, many regulations demand tamper-proof logs and strict control over sensitive data. A log proxy helps with on-the-fly redaction — scrubbing out personal information — while also ensuring no logs go missing in transit. Having a single, consistent log pipeline is a must for security audits and forensics.
Hybrid & Multi-Cloud Environments
Whether you’re using AWS, Azure, GCP, or on-prem servers, log proxies can unify logs across all these environments. This reduces complexity for organizations that have workloads running in multiple regions or clouds, ensuring a uniform approach to logging and compliance.
Architecture & Data Flow
Unlike a forward or reverse proxy that sits right in the traffic path, a log proxy collects logs from stdout streams, log files, or operating system logging services (like journald). Because it’s out-of-band, it doesn’t interfere with real-time user requests.
The processing of logs generally follows a similar pattern:
- Collection: Gather logs from local file paths, containers, or syslog daemons.
- Filtering & Parsing: Remove unneeded noise, parse text into structured fields (JSON, for instance).
- Enrichment: Add timestamps, container labels, environment tags, or anonymize fields containing PII.
- Buffering: Queue logs to avoid losing them if your network or logging platform is down.
- Forwarding: Send the logs to a centralized system like Elasticsearch, Splunk, or a cloud logging service.
Some teams prefer to do heavy lifting at the node level (for example, only shipping highly curated logs). Others do minimal processing locally, shipping raw data to a central aggregator for parsing. There’s no single “best” approach; it depends on how heavily you value bandwidth efficiency versus CPU overhead on each node.
Well-Known Tools and Services
If you’re considering a log proxy, you’ve likely come across a few names:
- Fluent Bit / Fluentd: Widely adopted in container ecosystems like Kubernetes. Fluent Bit is lightweight, while Fluentd is more full-featured.
- Logstash: Part of the Elastic Stack (ELK). Handles complex parsing, enrichment, and routing.
- Vector: A Rust-based solution known for its high performance and minimal memory usage.
- Elastic Beats (Filebeat, Metricbeat, etc.): Specialized shippers for file logs, metrics, or Windows Event Logs, each dedicated to a specific data type.
- Splunk Forwarder: Proprietary agents that forward logs into Splunk. Great for enterprise-scale deployments.
- Syslog-ng/rsyslog: Longstanding open-source projects in the Linux world for collecting, forwarding, and transforming syslog data.
- Grafana Agent: Part of the Grafana ecosystem, can send logs to Grafana Loki or metrics to Prometheus.
Potential Misconceptions
A log proxy isn’t built to hide anyone’s IP or bypass restrictions. It’s just aggregating data that’s already been generated. There’s no real-time network traffic interception happening.
While logs can include metrics (like how much bandwidth a user consumed), using a log proxy for real-time billing or quota enforcement isn’t typical. Providers typically rely on direct network measurements for that. A log proxy simply collects data that can be analyzed after the fact.
Conclusion
In summary, log proxies (a.k.a. log forwarders or logging agents) play a foundational role in modern observability practices. They centralize logs from a multitude of sources, standardize and enrich the data, and buffer against network disruptions—without ever sitting in the path of user traffic.
They differ greatly from more commonly discussed proxies like forward or reverse proxies, primarily because they don’t anonymize or mediate user traffic. Instead, they unlock reliability, security, and insight by consolidating crucial logs for further analysis.
Key takeaways about log proxies:
- They operate out-of-band
- Centralize log aggregation
- They can enrich and redact logs
- They allow buffering
- Log proxies aren’t anonymizing
Whether you’re deploying microservices in Kubernetes, ensuring compliance in a regulated industry, or just aiming for a more organized approach to troubleshooting, adopting log proxies can drastically simplify your life. They provide a backbone of clarity, ensuring your logs are always exactly where you need them — centralized, enriched, and ready for whatever analysis or alerting pipeline you run next.




