When it comes to online security and privacy, SOCKS proxies are an essential tool. But what exactly are SOCKS proxies and how do they work? If you’re unfamiliar with this term, you’re not alone. SOCKS proxies are often overlooked and misunderstood. In this comprehensive guide, we will talk about all things SOCKS and provide you with all the information you need to know.
What Is a SOCKS Proxy and How Does it Work?
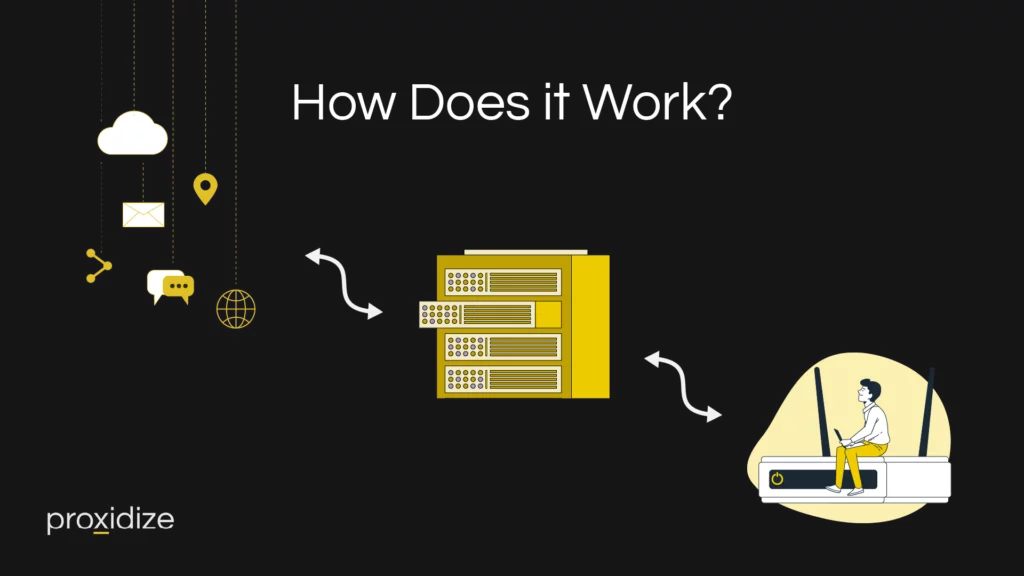
A SOCKS proxy is a tool that allows you to route your internet traffic through a remote server, providing you with anonymity and the ability to bypass restrictions. It acts as a mediator between your device and the websites or services you want to access. When you send a request to access a website, the request is first sent to the SOCKS proxy server.
The proxy server then forwards your request to the website on your behalf, using the SOCKS protocol. This protocol enables the proxy server to establish a TCP connection with the website and pass the data between the two. By using a SOCKS proxy, your real IP address is hidden, and your network traffic appears to be originating from the proxy server, enhancing your online privacy. Additionally, they support various authentication methods, ensuring secure communication between your device and the proxy server.

What Are the Different Types of SOCKS Protocols?
Now let’s talk about the different types of SOCKS protocols: SOCKS4 and SOCKS5. SOCKS4 is an older version that only supports IPv4 addresses and lacks authentication features. On the other hand, SOCKS5 is the newer and more advanced protocol that supports both IPv4 and IPv6 addresses, offers better authentication options, and provides additional features like UDP support.
SOCKS4 Proxy
SOCKS4 is one of the earliest versions of the SOCKS proxy servers. When you connect to the internet through a SOCKS4 proxy, your original IP address is replaced with the IP address of the proxy server. This provides a layer of anonymity and online security.
SOCKS4 proxy servers are commonly used by individuals and organizations to access restricted content or bypass internet censorship. Additionally, SOCKS4 proxies are known for their faster download speeds compared to other types of proxies. They are suitable for various types of traffic, including SMTP and FTP.
SOCKS5 Proxy
SOCKS5 is the latest version of the SOCKS network protocol, and it offers several advantages over its predecessor, SOCKS4. One of the key improvements is the ability to handle various types of network traffic, including TCP and UDP. SOCKS5 proxy servers also support authentication, allowing you to secure your online activity.
Additionally, it provides better support for mobile proxies and allows you to modify packet headers, giving you more control over your connection settings. Another advantage of SOCKS5 is its ability to establish a reliable connection, even through firewalls. It can also be used in conjunction with an SSH tunnel to create a secure and encrypted connection, further protecting your privacy.
What are the Pros and Cons of SOCKS Proxies?
There are several advantages and disadvantages of using SOCKS proxies, some include:
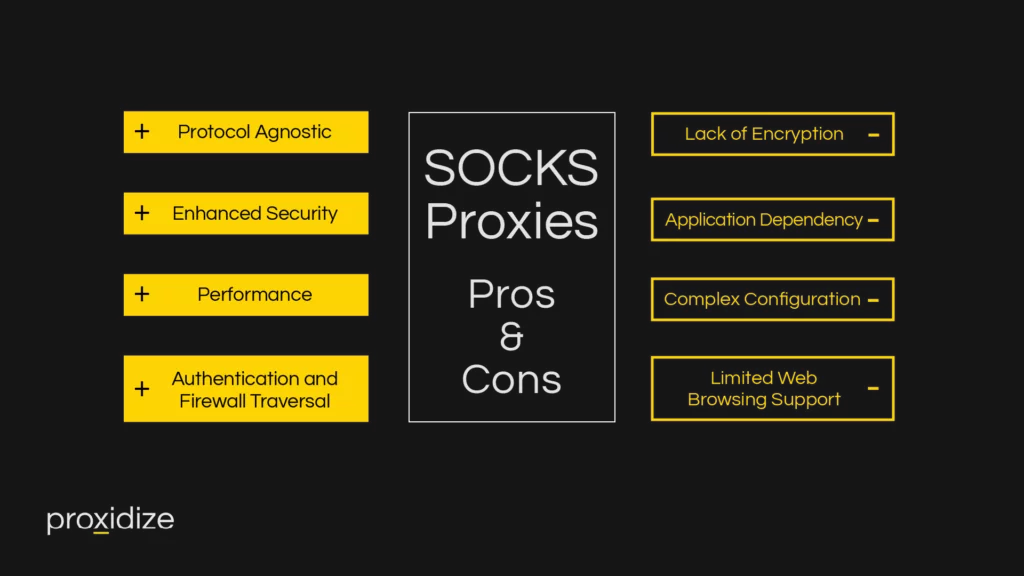
Pros:
- Protocol Agnostic: SOCKS proxies are protocol-agnostic, meaning they can handle various types of internet traffic. This flexibility allows for seamless support across different applications and protocols.
- Enhanced Security: SOCKS proxies operate at a lower level than HTTP proxies, making them suitable for a wide array of traffic. This lower-level operation can contribute to enhanced security, especially when dealing with applications that require advanced encryption.
- Authentication and Firewall Traversal: SOCKS proxies support authentication, providing an additional layer of security. They also facilitate traversing firewalls, making them suitable for scenarios where internet access is restricted.
- Performance: SOCKS proxies generally exhibit better performance than HTTP proxies, especially for applications that demand real-time data transfer, like online gaming or video streaming.
Cons:
- Lack of Encryption: Unlike HTTPS proxies, SOCKS proxies do not inherently provide encryption. While they facilitate traffic redirection, the lack of encryption makes data vulnerable to interception. For secure transmissions, additional encryption layers may be required.
- Limited Web Browsing Support: SOCKS proxies may not be the optimal choice for general web browsing. They lack the ability to interpret and modify HTTP content, limiting their effectiveness in scenarios where content modification is crucial.
- Application Dependency: SOCKS proxies rely on applications to be SOCKS-aware. Not all applications support SOCKS natively, which may pose a challenge in situations where comprehensive proxy support is essential.
- Complex Configuration: Configuring SOCKS proxies can be more complex compared to HTTP proxies, especially for users who are less familiar with networking concepts. This complexity might pose challenges in certain deployment scenarios.
Understanding these pros and cons is crucial for making informed decisions about the suitability of SOCKS proxies for specific use cases.

HTTP vs. SOCKS Proxies: Defining the Differences
Understanding the distinctions between HTTP (HyperText Transfer Protocol) and SOCKS proxies is essential for selecting the right proxy type based on specific use cases. Here’s a breakdown of the differences between the two:
HTTP Proxies:
- Application Focus: HTTP proxies are designed specifically for handling web traffic. They are optimized for web browsing, content retrieval, and interactions with web servers.
- Content Modification: HTTP proxies can interpret and modify web content. This feature is crucial for tasks like web scraping, content filtering, and altering HTTP requests and responses.
- Layer of Operation: HTTP proxies operate at the application layer of the OSI model. They are protocol-aware and can understand and manipulate HTTP/HTTPS traffic.
- Encryption Support: HTTP proxies often support HTTPS, providing an additional layer of security through encrypted connections. This is especially important for securing sensitive data during transmissions.
- Browser Compatibility: HTTP proxies are seamlessly integrated with web browsers. They require minimal configuration and are suitable for scenarios where user interaction with web content is a priority.
SOCKS Proxies:
- Protocol Agnostic: SOCKS proxies are protocol-agnostic, meaning they can handle various types of internet traffic beyond HTTP. They operate at a lower level, making them suitable for diverse applications and protocols.
- Encryption Handling: SOCKS proxies do not inherently provide encryption. While they can redirect encrypted traffic, the encryption itself is managed by the applications or protocols in use.
- Application Independence: SOCKS proxies don’t require applications to be SOCKS-aware. They function at a lower level and can redirect traffic for any SOCKS-compatible application, providing more flexibility.
- Firewall Traversal: SOCKS proxies are effective at traversing firewalls. They can facilitate connections even in situations where direct connections might be restricted.
- Performance: SOCKS proxies generally offer better performance, particularly for applications requiring real-time data transfer. This makes them suitable for scenarios like online gaming or video streaming.
Choosing Between HTTP and SOCKS:
Web-Centric Tasks
- HTTP: Opt for HTTP proxies when the primary focus is on web-centric tasks such as web scraping, content modification, or general web browsing.
Diverse Protocols
- SOCKS: Choose SOCKS proxies for scenarios involving diverse protocols, applications that aren’t HTTP-centric, or situations where protocol flexibility is crucial.
What Is SSH Tunneling?
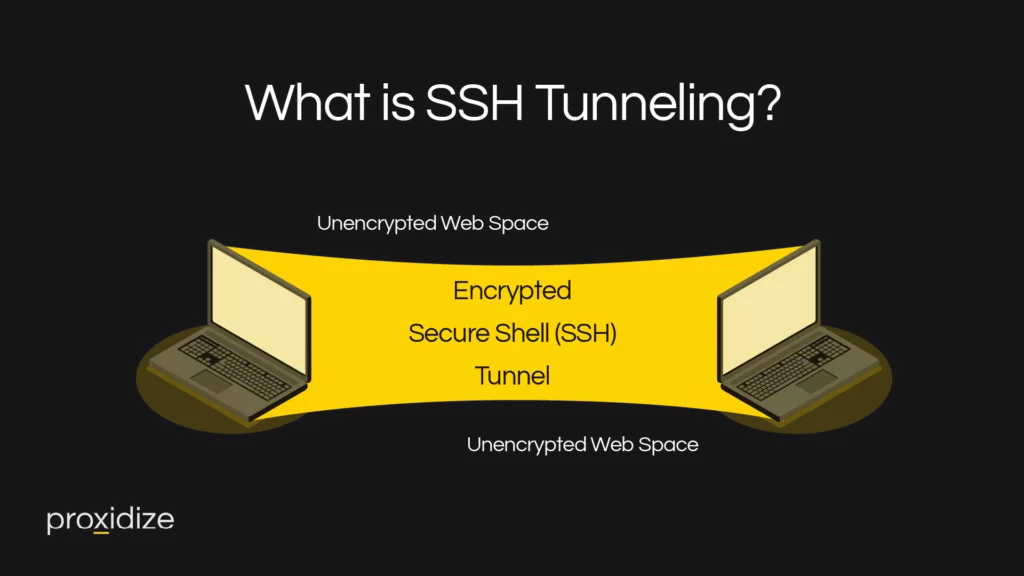
To understand SSH tunneling, you need to grasp the concept of secure communication channels. SSH, which stands for Secure Shell, is a cryptographic network protocol that provides a secure way to communicate between two devices over an unsecured network. It establishes an encrypted connection, preventing any unauthorized access or tampering of data.
SSH tunneling takes advantage of this secure connection to create a tunnel between a local and a remote machine. This tunnel can be used to securely transmit data, bypass network restrictions, or access resources on a remote network. SSH tunneling works by encapsulating the data within the SSH connection, effectively hiding it from prying eyes. This technique has become increasingly popular for securing sensitive data and ensuring privacy in various applications.

Why Use SSH with SOCKS?
Using SSH with SOCKS provides an added layer of security and flexibility for your network connections. By combining the secure shell (SSH) protocol with SOCKS proxies, you can encrypt and protect your data while also bypassing network restrictions. SSH acts as a secure tunnel, encrypting your traffic and preventing unauthorized access to your information.
This means that even if someone intercepts your connection, they won’t be able to decipher the data. Additionally, SSH with SOCKS allows you to access restricted websites or services by routing your traffic through a proxy server. This is particularly useful if you are in a location where certain websites or services are blocked. With SSH and SOCKS, you can enjoy a secure and unrestricted browsing experience.
Conclusion
In conclusion, SOCKS proxies are a useful tool for enhancing online security and privacy. They allow you to mask your IP address and encrypt your internet traffic, making it harder for others to track or monitor your online activities. While there are some legal considerations to keep in mind when using SOCKS proxies, their benefits, such as bypassing restrictions and accessing blocked content, make them a popular choice for many internet users.






