In this article, we’re going to take a look at transparent proxy servers, a key component in network management. You’ll learn what they are, how they work within a network, where they’re applied in the real world, and the pros and cons compared to other network management solutions.
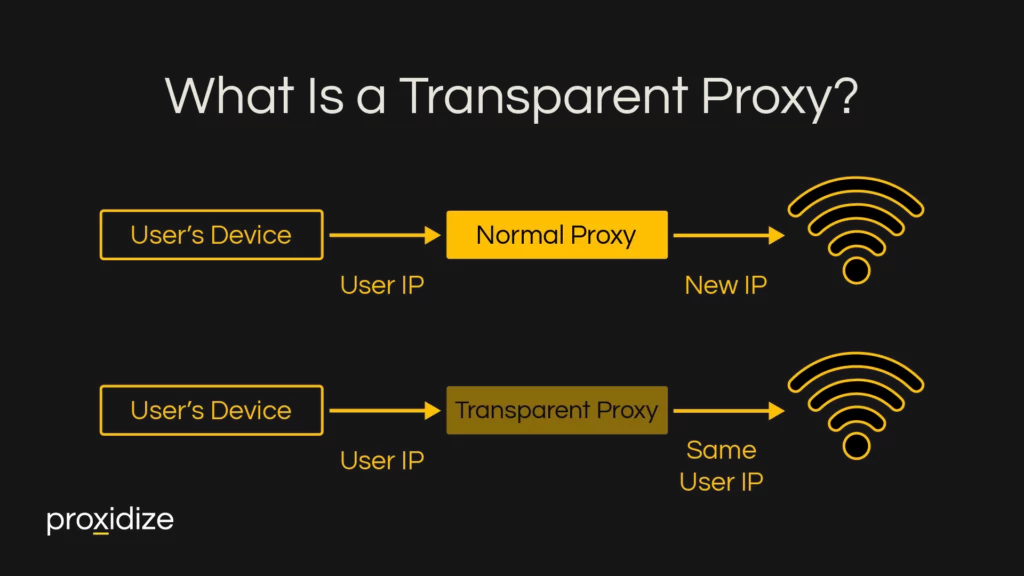
What Is a Transparent Proxy?
A transparent proxy, also known as an inline, intercepting, or forced proxy, is a server that sits between a user’s device and the internet. It’s called “transparent” because it intercepts and manages web traffic without changing its IP, unlike other proxies. It also doesn’t require any configuration on the end-user’s device. This proxy type filters content, authenticates users, caches data, and can monitor and log internet activities.
Transparent proxies differ from traditional proxies in two significant ways. Firstly, a transparent proxy works at the network infrastructure level. This means that it manages traffic for all users connected to the network, unlike traditional proxies, which are client-side proxies and require configuration on a user’s device. Secondly, because it works at the network level, it can operate without the user’s knowledge, although welcome messages and usage policies will often appear when connecting to such a network.
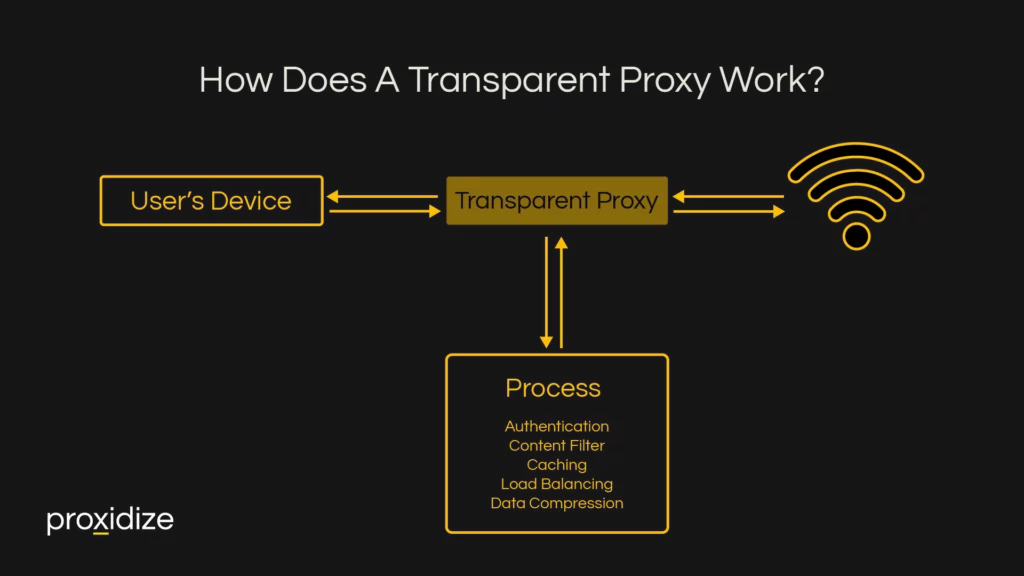
How Does a Transparent Proxy Work?
A transparent proxy works by intercepting a request for a connected user’s device, applying checks like content filters, caching, and authentication, and then sending the data received from the internet back to your device.
- Request: When you access a website or service online, your device sends out a request. This request is like a digital message asking to retrieve data from the internet.
- Transparent Proxy Intercepts: As this request travels through the network, a transparent proxy server automatically intercepts it. This interception is silent and invisible to you as a user.
- Process:
- Content Filter: The proxy checks the request against rules for allowed or blocked websites. If the site is inappropriate or unsafe, the proxy blocks access.
- Caching: If the content you’re requesting is already stored on the proxy (cached), it will be quickly delivered from there, reducing load times.
- Authentication: In some networks, the proxy also checks if the request comes from an authorized user.
- Load Balancing: The proxy can also perform load balancing. It assesses the network’s servers and directs the request to the one that is best positioned to respond quickly and efficiently. This ensures no single server is overloaded and optimizes network performance.
- Data Compression: After filtering content and before forwarding requests, the transparent proxy can compress the data, which speeds up the transmission of data, and is especially helpful in situations where bandwidth is limited.
- Forward Request: If the site is allowed and not cached, the proxy forwards your request to the intended web server on the internet.
- Receive Response: The web server processes the request and sends the information back. This response first arrives at the transparent proxy.
- Return Data to Device: The proxy then relays the web server’s response back to your device, allowing you to view the website or use the online service.
Common Applications and Environments
Transparent proxies are most relevant in environments where an establishment has many people, whose devices it doesn’t have access to, connecting to the same network. The proxy would serve as a blanket method to filter content, monitor internet use, and enforce network use policies. This is especially true for public WiFi networks intended for “guests”.
Several types of organizations fit this description:
- Corporate Offices: To enforce internet usage policies and secure corporate data. Most effective when the company does not have control over individual devices connected to its network and has to manage a large number of users.
- Educational Institutions: Schools and universities can enforce content filters and monitor student internet usage.
- Public Libraries: To filter content for a wide range of users and ensure appropriate use of resources.
- Hotels and Hospitality Venues: Offering guest WiFi while managing network security and content access.
- Hospitals and Healthcare Facilities: To secure patient data and control network use.
- Airports and Transit Hubs: Providing public WiFi with content filtering and usage monitoring.
- Retail and Shopping Centers: Offering customer WiFi with content control and data security.
- Government Buildings: Enforcing strict internet use policies and ensuring secure communication.
- Internet Cafés: Managing public internet access and maintaining network security.
Advantages & Disadvantages of Transparent Proxies
As we’ve previously stated, transparent proxies are at their best when there’s a need to enforce a network-wide policy and content filtering across many users without access to individual users’ devices or if individually configuring them would be unfeasible. They also shine when the network has to handle large volumes of traffic and optimization is required. Finally, they’re effective in circumstances when internet usage has to be monitored for security or compliance purposes. They don’t require configuration on the users’ end, which significantly simplifies network management.
A key drawback of transparent proxies is their general effect on the entire network. Individual users can’t be given different levels of access or be offered different content filter rules, which limits their use of network-wide applications like at a public library.
Additionally, their incorrect application can have a detrimental effect on the user experience. For example, if the proxy server’s hardware or software can’t handle high traffic volumes efficiently, this can lead to delayed response times and slow internet speeds for users. This is especially true in scenarios with extensive content filtering or complex rule sets, where each request demands significant processing.
Furthermore, transparent proxies that manage encrypted HTTPS traffic can introduce risks if the decryption and re-encryption processes are not secure. This could potentially expose sensitive data to interception. Additionally, improper configuration can leave the proxy vulnerable to various cyber-attacks.
Finally, some network protocols and applications expect a direct, unimpeded connection to their servers. VPNs, certain streaming services, or specialized communication protocols might not work or work suboptimally if they’re routed through a transparent proxy.
This makes it particularly important to configure a transparent proxy correctly and test it thoroughly. Particularly the last aspect is somewhat mitigated by the likely public nature of the network — some connectivity is better than none at the airport.
Transparent proxies have the capacity to be invisible to the end user, which makes it important to convey through a welcome screen, signage, and more, that users who connect to the network will be subject to the proxy.
Alternatives to Transparent Proxies
The reason the use cases for transparent proxies are so specific — “guest” networks — is because many alternatives exist to achieve the same effect. Many of these require much less technical knowledge to set up, are more user-friendly, and/or offer a greater range of customization options.
- Firewalls: Unlike transparent proxies, firewalls focus mostly on security. They monitor incoming and outgoing network traffic and decide whether to allow or block specific traffic based on a defined set of security rules.
- Content Filtering Software: Installed directly on individual devices, this software offers more precise control over internet access. It can block or allow specific websites and content types based on user profiles, making it ideal for personalized content management. This is a more relevant option for most companies, for example.
- DNS-Based Filtering: This method involves controlling website access by modifying DNS responses. It’s simpler than a transparent proxy and is effective for quickly blocking access to specific domains or websites.
- Endpoint Security Solutions: These are security programs installed on each user’s device. They typically include antivirus, anti-malware, and web filtering options, which gives the administrator greater possibilities for individual customization.
- Cloud-Based Security Services: These services, offered over the internet, provide various security functions like content filtering, threat detection, and data protection. They are easy to scale and maintain, as they don’t require on-premise hardware. Many of these also offer additional features such as email tracking and audit logs.
- Router Configuration: Some advanced routers come with built-in security and content-filtering features. This allows for network-level control similar to a transparent proxy but is often less complex to set up and manage.
- Network Access Control (NAC) Systems: NAC systems manage and enforce policy on devices attempting to access the network. They can grant or deny access based on compliance with security policies, providing a different approach to managing network use.
Conclusion
We’ve discussed transparent proxies in-depth, explaining how they work, where they fit in network management, and their pros and cons. With this understanding, you should have a clearer picture of how transparent proxies can be a valuable tool in various network environments. Despite the greater technical knowledge required to establish, transparent proxies can be a powerful tool for managing high-traffic networks with a large number of users.