In the world of web automation, the need to anonymize your presence online can take on multiple dimensions. At the purely network level, one can use proxies; at the browser level, one can turn to antidetect browsers and headless browsers; but what if you wanted to take it a step further? A virtual machine is a way to compartmentalize your automation at the system level.
A virtual machine is a way to emulate a computer system. It creates a virtual environment that operates as if it were its own computer, complete with its own set of hardware resources. VMs are a versatile tool used in everything from testing and development to penetration testing and cloud infrastructure. We’ll be looking at them through the lens of anonymity and automation.
In this article we’ll explore what virtual machines are, how they work, give you a step-by-step guide on how to set one up, and explore where they fit among other anonymizing and privacy software.

What are Virtual Machines?
Virtual machines, or VMs, are emulation software that run on their own operating system. A VM works similarly to a physical machine, to which you allocate a portion of the physical device’s hardware, i.e. CPU, memory, storage, internet connection, etc. The VM then operates as if it were a physical computer with those specs.
A VM requires its own OS, too, along with any software you want to use on it — it can’t pull data from its host by default. This isn’t dual-booting, where one computer has two operating systems installed; it’s a Windows computer running a virtual machine which runs Ubuntu, for example.
The computer the VM is running on is called the physical host machine, host computer, host OS, or just the host. The VM itself is referred to as a guest machine, guest computer, guest OS, or just guest.
How do Virtual Machines Work?
A VM offers an isolated environment separate from the host device, operated via its own OS. A single device is capable of running multiple VMs all with different operating systems and applications without affecting or interacting with each other.
VMs are still dependent on the host’s resources as the host’s hardware is what creates and handles the virtualization. This makes it possible to run many different environments at the same time and accommodate fluctuating workloads. For the user, the VM works just like the host machine. Resources such as the CPU, memory, and storage appear as they would on a host — although limited to the amount allocated to it.
When running a VM, it appears as any application window would, able to be dragged around, minimized, etc. Your VM has to be explicitly told it can “see” the input devices like a keyboard and mouse plugged into the host machine, though.
Several key files make up a system VM:
- Log file: As the name suggests, the log file is where all the activity of the VM is logged.
- NVRAM setting file: The non-volatile RAM file stores all the data the VM needs even when it’s turned off, similar to the host device’s NVRAM or BIOS settings.
- Virtual disk file: The virtual disk file is the VM’s hard drive, storing all the data that would be stored on a hard drive if it were a physical device.
- Configuration file: The config file stores all the limitations of the VM, how much of the host device it’s allowed to use, etc.
Directing all of this activity is software called the hypervisor or virtual machine monitor. This is what oversees the resources allocated to the VM by the host, interfacing between both while ensuring they remain strictly compartmentalized from one another.
Types of Virtual Machines
There are two primary types of virtual machine, which differ in the scope of their emulation and serve different purposes. These are:
System Virtual Machines
System VMs most closely match what we have so far described in this article. They are hosted on a physical server and run their own operating system. A VM shares the host’s physical resources and provides a complete environment for running applications and services, emulating a physical machine.
The convenience of a VM is that it’s easily deployed, cloned, and scaled up or down. It works across different platforms and multiple VMs can be managed from a single location.
Process Virtual Machines
A process virtual machine is a platform-independent environment for running a single process or program. It only exists as long as the program is running and then shuts down. Instead of emulating a whole device with its own OS and hardware, it creates a consistent environment so that the program doesn’t need to account for differences between hardware and operating systems.
By not emulating an entire device, the virtualization is much more lightweight, requiring far fewer resources, without exposing the host OS to any risk the program might pose (although this doesn’t protect against hardware-level threats, for example).
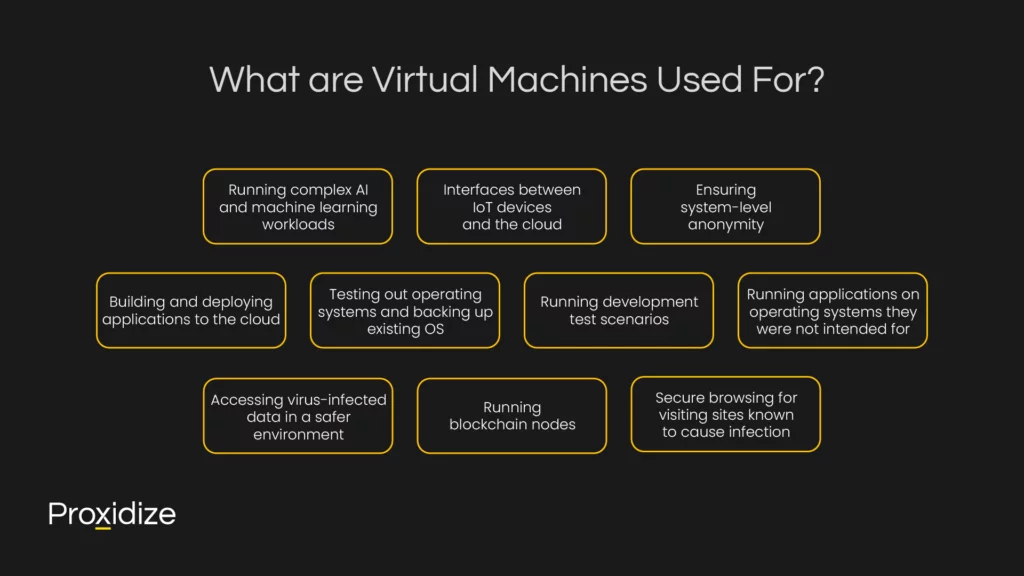
What are Virtual Machines Used For?
One of the most common use cases of virtual machines involves testing out software. Developers need to test their software on different operating systems, and VMs offer a convenient way to run programs on a different OS. Another use case is related to security; by running a program in an isolated environment, no harm can come to the host. Here are some other common use cases for VMs:
- Building and deploying applications to the cloud
- Testing out operating systems and backing up existing OS
- Running development test scenarios
- Accessing virus-infected data in a safer environment
- Running software or applications on operating systems that they were not intended for
- Secure browsing for visiting sites known to cause infection
- Act as gateways for IoT devices to provide secure and manageable interfaces between devices and the cloud
- Running complex AI and machine learning workloads
- Running blockchain nodes by providing isolation and easy management for distributed ledger technologies
- Ensuring system-level anonymity
How to Set Up a Virtual Machine
There are several virtual machine providers online including the VirtualBox for Windows, Linux, and macOS, VMware Player for Windows and Linux, VMwareFusion for the macOS, and Parallels Desktop for the macOS. We will be covering how to install and run the VirtualBox system.
For starters, there are a few requirements to run a VM:
- A computer that supports virtualization
- A minimum of 8-20 GB of desk space and 1 GB of RAM
- Installation Media (this could be a CD or a .iso file)
- A product key (if the VM OS is Windows)
- An internet connection
Once you have these, follow this guide.
Step 1: Download and Install VirtualBox. Select the version for the host’s operating system. After doing so, a prompt will appear to install several Oracle components. It is recommended to install all of them.
Step 2: Create a Virtual Machine. Click on the “New” button in the menu and enter the name of the VM. This will assist with identifying it and differing it from other VMs that might be created. Select the type and version depending on the OS that is going to be used.
Step 3: Assign a memory limit. This limit should not be more than half of the available RAM of the host. For a Windows or macOS VM, use at least 1–2 GBl for Linux VM use at least 512 MB.
Step 4: Setup the hard drive. This will be a virtual hard drive separate from the host.
Step 5: Select the VDI hard drive file type. This will store the VM in a single file with a .vdi extension.
Step 6: Select a storage space on the physical hard drive. By selecting “dynamically allocated” you can save space on the host. Selecting “fixed size” might produce better performance but will take up much more space.
Step 7: Setup the file location and size. VirtualBox does this by default but depending on your use case you might want a larger size. Keep in mind that this will be using space on your computer, so allocate accordingly.
Step 8: Install the OS. Double click on the VM and browse to the installation media or the .iso file. The installation process will change depending on the OS of choice.
Step 9: Install Guest Additions. These add more functionality to the VM such as the option to make the VM fullscreen. It is recommended to install guest additions in safe mode on Windows devices in order to enable 2D and 3D accelerations.
Step 10: Update the setting for 2D and 3D acceleration. Enter the display settings for the VM, check both the 2D and 3D acceleration settings, and increase video memory. Once all that is done, launch the VM.
Additional Optional Step: Implement a proxy. Within VirtualBox’s manager settings, you can implement a proxy. This adds a level of anonymity at the network level, with all the features a proxy server provides.
Conclusion
By emulating an entire computer system in an isolated environment, virtual machines allow you to compartmentalize further than a proxy or antidetect browser would alone. The ability to section off a part of your device facilitates their broader use in software development, testing, and security and makes them powerful, versatile tools across the board.
Setting up a VM is straightforward — even for a non-technical enthusiast — and is a low-impact way to use multiple operating systems on your computer. In this article we have offered a basic introduction on what VMs are, where they fit among anonymizing software, and sketched an overview on what they can be used for.
In subsequent articles, we’ll explore their place among anonymizing software more in-depth, as well as the overlap between the use cases of VMs and proxies.






